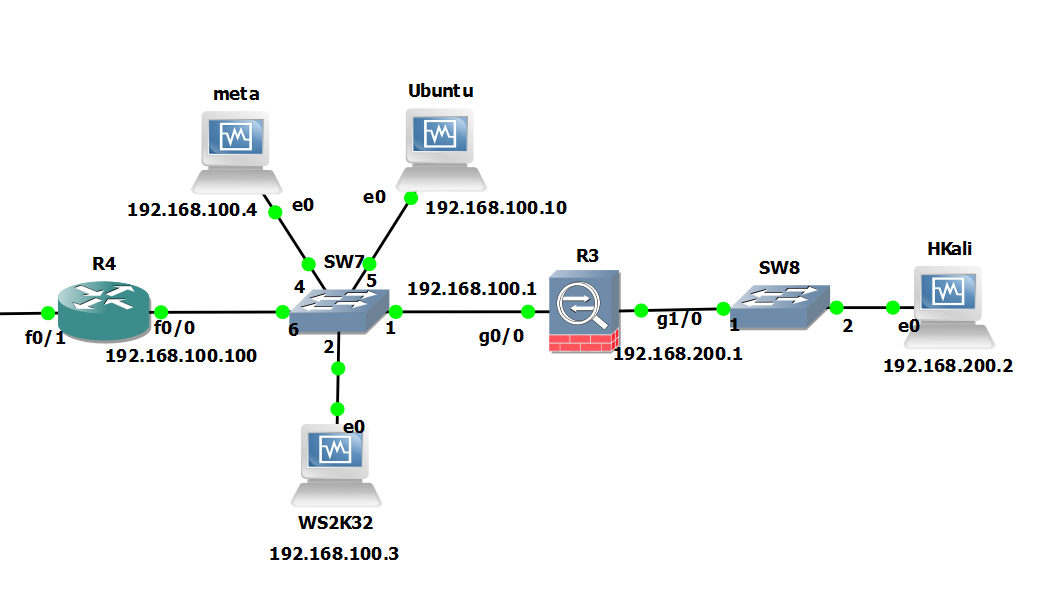
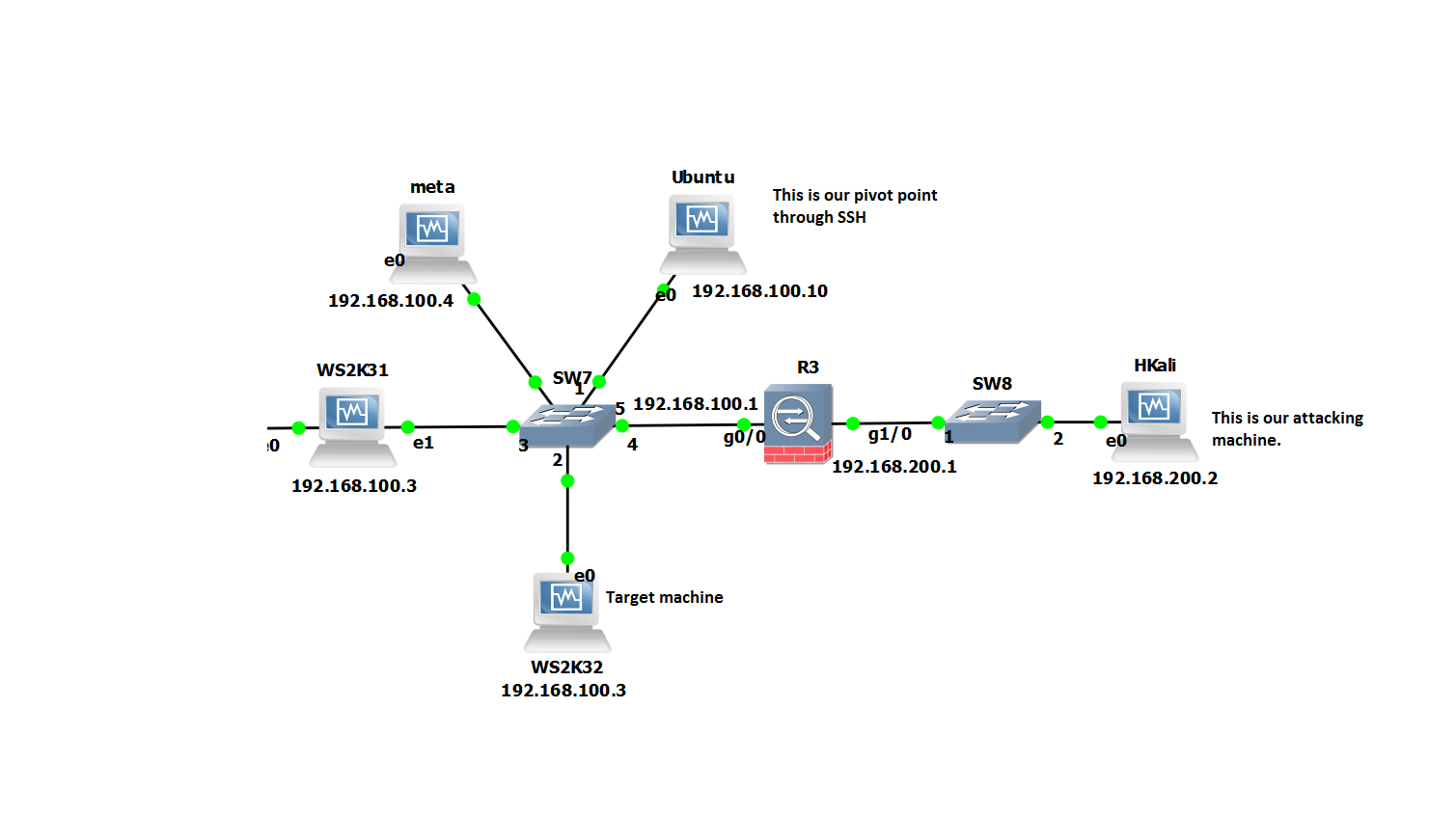
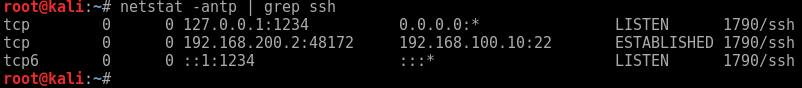
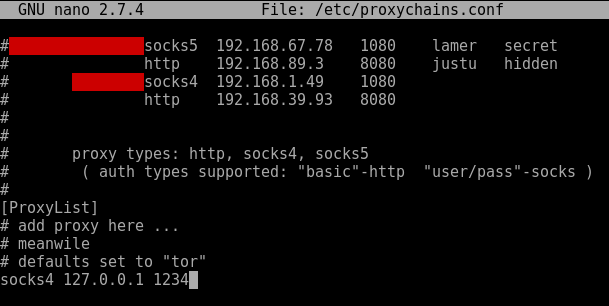
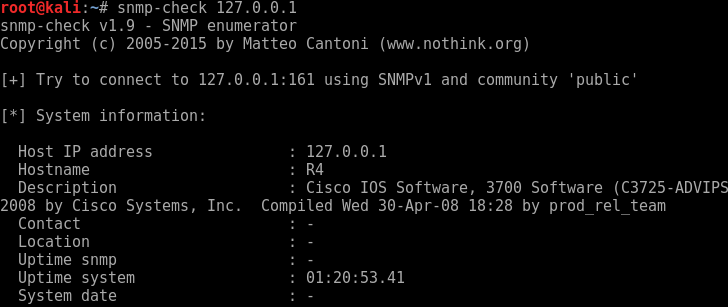
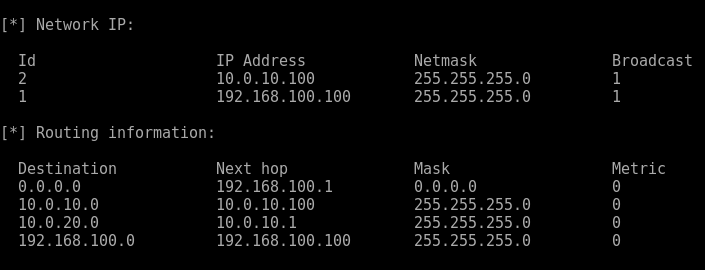
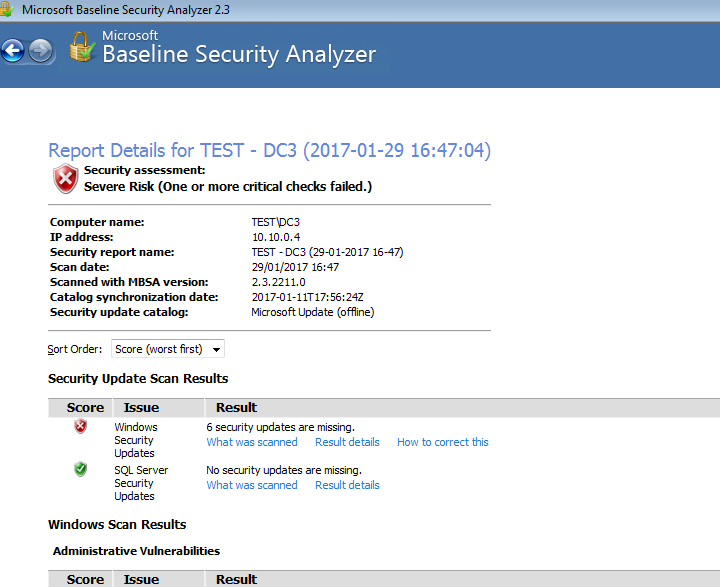
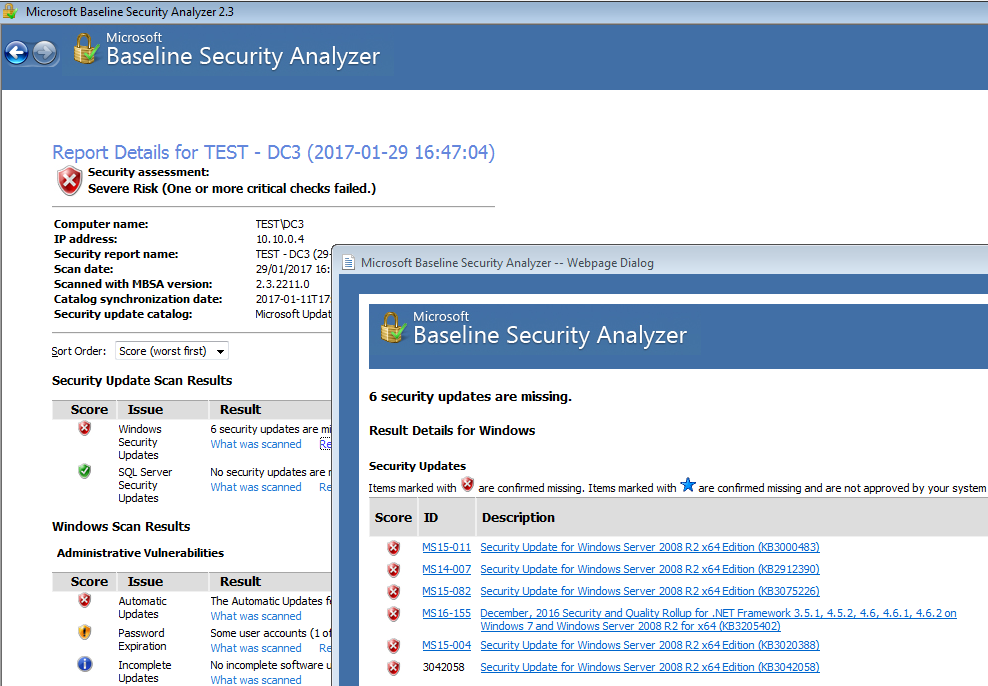
How to create realistic test user accounts in Active Directory test lab. Often when I’m working through certain lab scenarios I will want multiple realistic test users in Active Directory to work with. Yeah sad I know. However, for example if searching through users in PowerShell, modifying permissions or pentesting techniques like RID cycling etc you would ideally want realistic users with pre-populated data to search through. Sure you can create a quick script to create a bunch of accounts like user1 user2 user3, with Address1 Address2 and Address3 however I prefer to have a realistic environment to work in. After all, by working in a lab ultimately we are trying to mimicking an Enterprise environment or order to test something your working on. I wanted a quick simple was to do this. I came across this website by Helge Klein which does the trick. A PowerShell script to create realistic users with proper account names, first name, surname, address etc. In order to create realistic accounts you do require the information such as names and addresses which Helge supply’s in the form of a few text files.
You need to set a few variables at the beginning of the script:
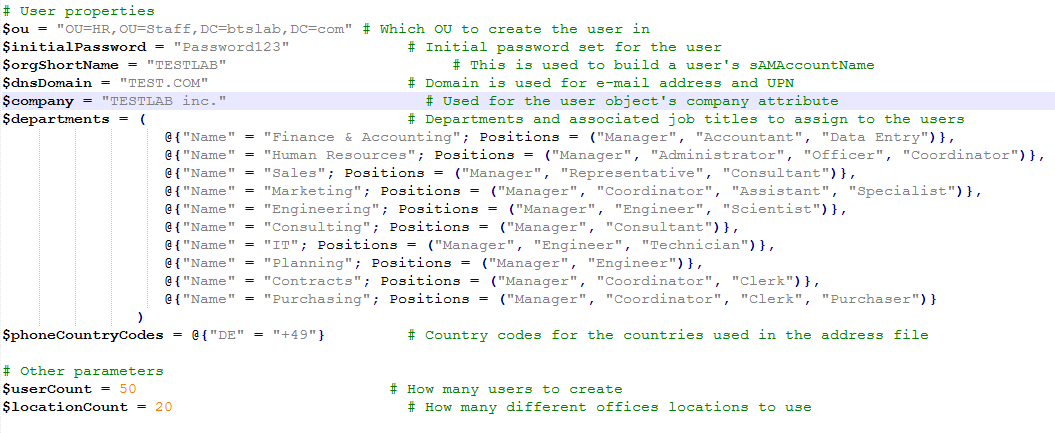
Note you can set the user count variable $userCount to the amount of users you want in your lab.
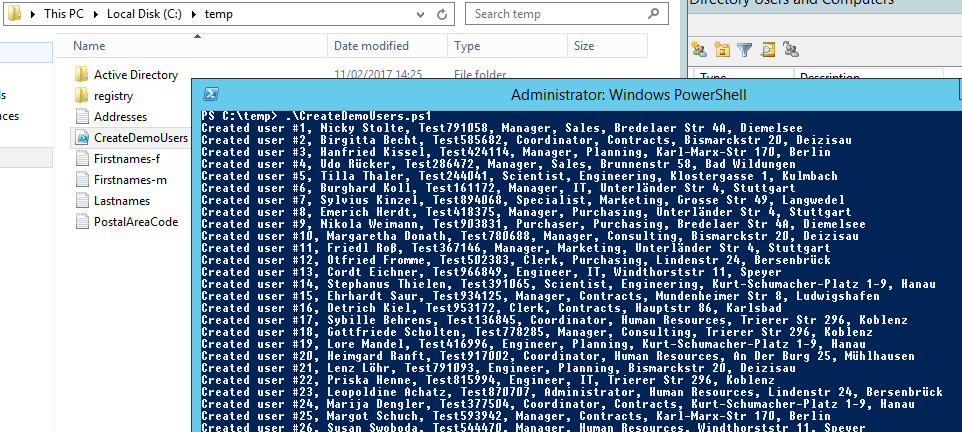
Running the script results in the following:
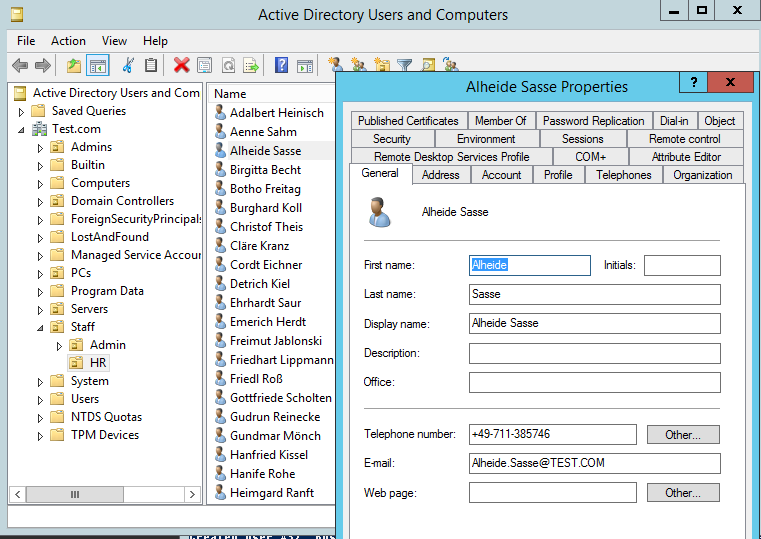
And as we can see in ‘Active Directory Users and Computers’ we have our test users:
As always familiarise your self with the script be comfortable with what its doing! enjoy!