Searching for password files in PowerShell
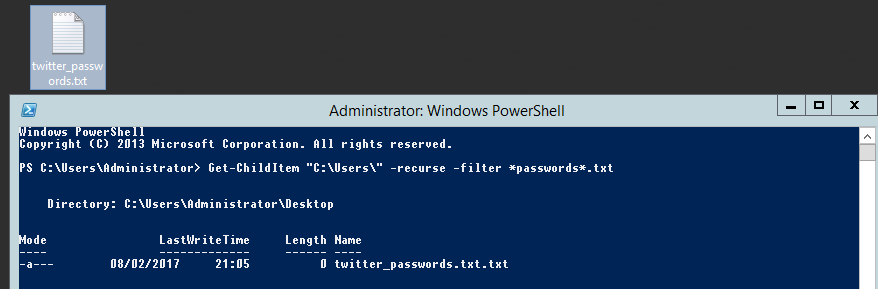
 Searching for password files in PowerShell, can be particularly useful especially for post exploitation recon phase of an engagement. PowerShell is great tool for a penetration tester. Its post exploitation capabilities has grown exceptionally over the last few years. During the course of a penetration test once you have compromised a windows host there is a good chance that you will want to enumerate the host system further and gather as much information as possible. If you have access to a low privilege user you are likely going to want to escalation your privileges to higher account. This being known as post-exploitation. This will almost always likely include searching the local system for passwords. We will want to search for xlsx, docx are classics. Sure we can use the windows built-in gui however we can also use PowerShell. We can use the following syntax in PowerShell to search for files with the text ‘password’ in the filename, just like below. We use the wildcard ‘*’ either end of the ‘passwords’ so we can search for variations in the file name. Ace!
Searching for password files in PowerShell, can be particularly useful especially for post exploitation recon phase of an engagement. PowerShell is great tool for a penetration tester. Its post exploitation capabilities has grown exceptionally over the last few years. During the course of a penetration test once you have compromised a windows host there is a good chance that you will want to enumerate the host system further and gather as much information as possible. If you have access to a low privilege user you are likely going to want to escalation your privileges to higher account. This being known as post-exploitation. This will almost always likely include searching the local system for passwords. We will want to search for xlsx, docx are classics. Sure we can use the windows built-in gui however we can also use PowerShell. We can use the following syntax in PowerShell to search for files with the text ‘password’ in the filename, just like below. We use the wildcard ‘*’ either end of the ‘passwords’ so we can search for variations in the file name. Ace!
Get-ChildItem "C:\Users\" -recurse -filter *passwords*.txt
Simple, quick and very effective, this needs to be in your cheetsheet!