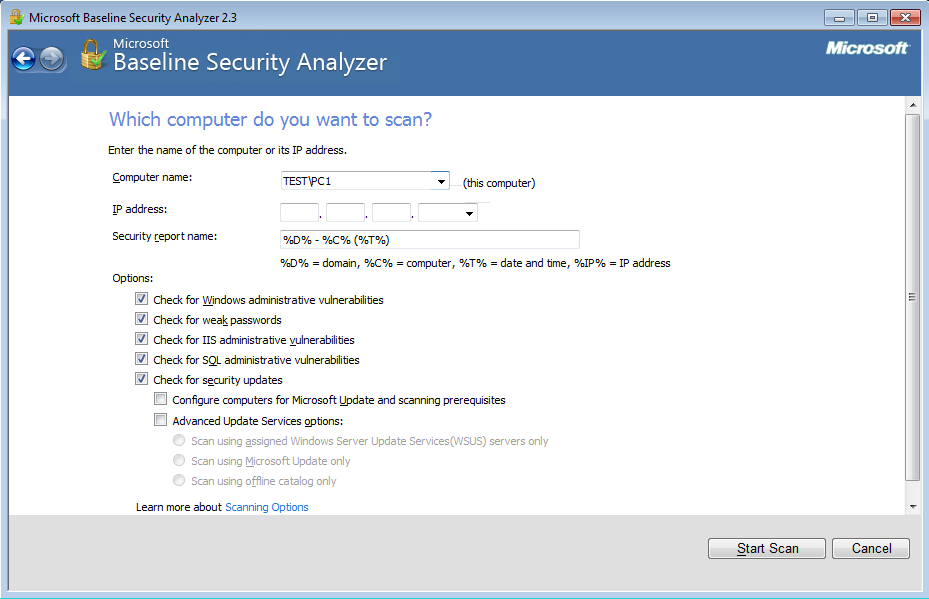
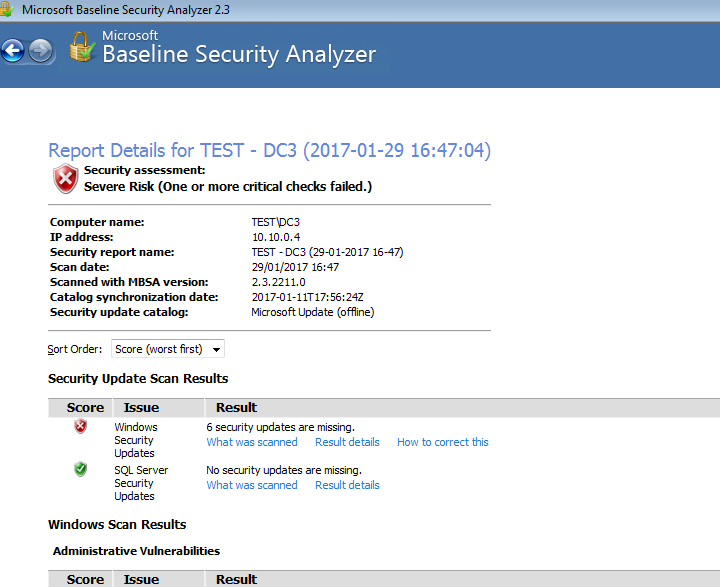
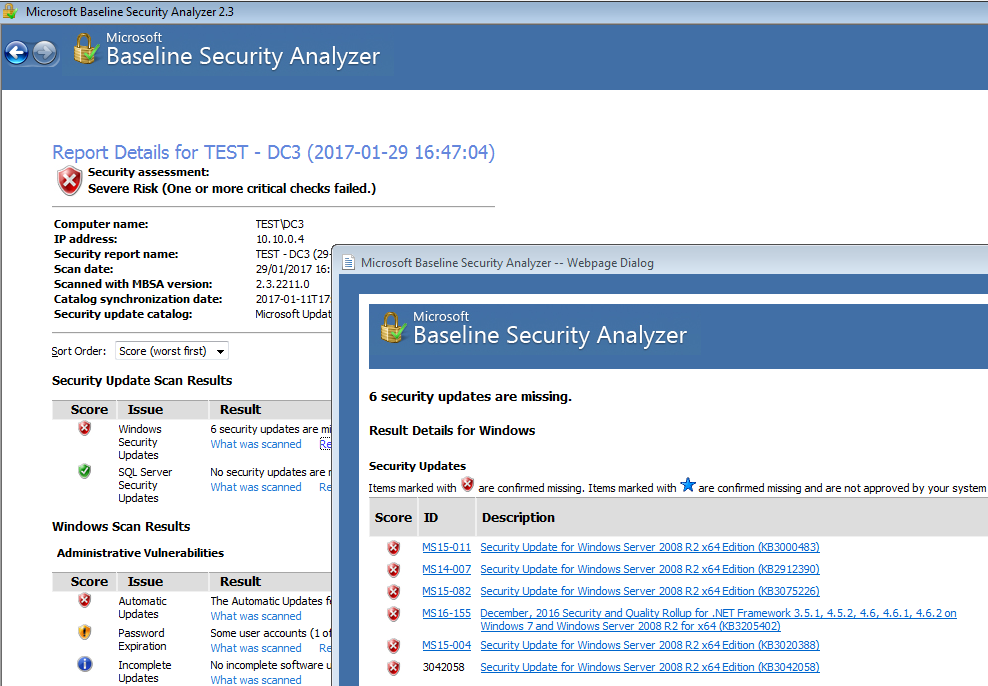
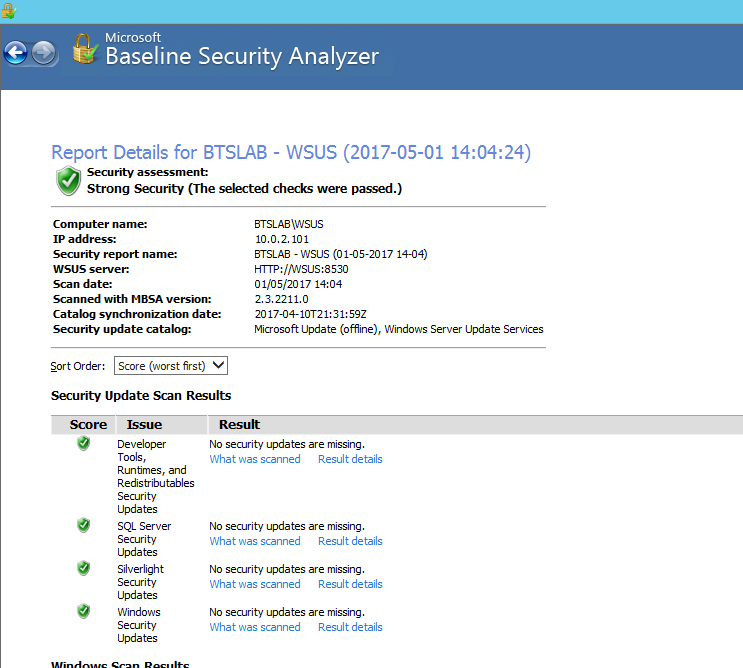
Are you having difficulty with your WSUS clients not reporting in? I recently posted about running Microsoft Baseline Security Analyser to check your systems are getting the right patches in this post. If your haveing issues with clients not checking in this may help. If you have gone through the basic troubleshooting steps and believe you have everything in place continue on. In this instance we have recognised that our Automatic update agent store is corrupt or that your clients may have a matched susclient ID in WSUS. More info on troubleshooting the basics first can be read about in this article by Microsoft.
This script will help your clients check back in to WSUS. If the agent store is corrupt or the client agent susclient id is botched. In my experience that a few other issues this tends to be the most common issue that crops up. Issues with Clients having the Same SUSclient ID usually happens as a result of an imaging process.
Save the below txt into a batch file, then run with elevated privileges in an Administrative command prompt on your target machine.
REM stop the Windows Updates service net stop wuauserv REM Delete SusClientID and AccountDomainSid registry keys SET WU_KEY=HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate reg delete %WU_KEY% /v SusClientID /f reg delete %WU_KEY% /v AccountDomainSid /f REM Delete registry keys may contain old SUS info reg delete “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update” /f REM Start the Windows Updates service net start wuauserv REM Initiate the WU Client… wuauclt /resetauthorization /detectnow
Hope this helps as this can be frustrating waiting for clients to check back in.