Advanced Persistent Threats are becoming an increasingly prevalent threat to organisations and the information they hold. Advanced Persistent Threats are a type of attack that are defined by the National Institute of Standards and Technology (2011) as being a highly sophisticated attack, well-orchestrated, well-funded and are targeted at specific organisations or people. These type of attacks seek to gain a foothold inside an organisation, remain undetected and over a specific time frame from 
hours to months laterally move across the network and exfiltrate data, the specific information assets they desire undetected, often more than once. This is as opposed to the more conventional opportunist attacker who isn’t interested in any particular target or any specific data. If the attacker doesn’t succeed the first time they will simply move onto the next weakest victim, these types of attack have often in the passed been used only to heighten the profile of a hacker. Attack vectors include Spear fishing attempts with either email content or attachments carrying the payload through to malware and more commonly malvertising.
Evidence of high profile targeted Advanced Persistent Threats are being reported in the press more than ever. Some examples of such being Target’s 2013 breach, Sony 2014 breach and more recently Ashley Madison 2015 this list goes on. Upholding the confidentiality, availability and integrity of information that these sites and companies hold is possible through the use of good IT Governance. With an effective and current Information Security Management System in place and utilizing good strong controls organisations can better protect themselves from Advanced Persistent Threats.
Ensuring user awareness training is provided. Ensuring the desktop is appropriately secured. Keeping software up to date. Ensuring strong Authentication mechanisms are in place. Ensuring Antivirus, Firewalls and Host Intrusion Detection/Prevention systems are appropriately configured and kept up to date are all only some of the controls that should be in place as a standard to help mitigate the risk.
All too often perimeter defenses are in place and appropriately secured from the outside, however from inside out, the desktop and the actual user are all attack vectors that are left open to threats. The threat landscape is constantly evolving, we need to stay on top in order to try and evade APTs.
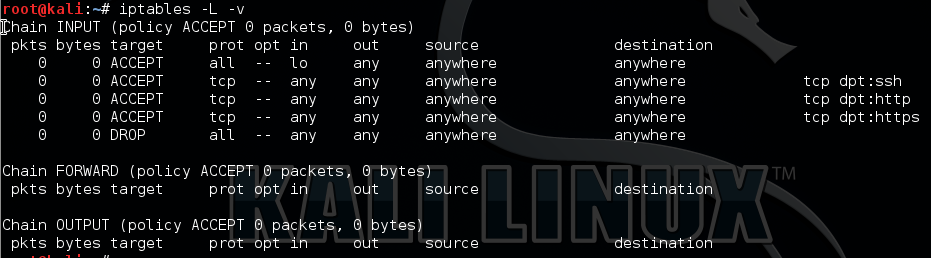
 Check out the Linux Firewall mini setup guide which demonstrates the use of iptables in Linux. Here I demonstrate a few basic commands and rules and explained how we can allow and deny specific traffic on your Linux server. The scenario is for typical web server allowing only HTTP, HTTPS and SSH. Host based firewalls are often overlooked relying solely on perimeter defenses however are an important aspect of protecting your endpoint whether that is on a server or workstation. Iptables in built into Linux is a pretty capable command line based stateful firewall. Once you have the hang on the syntax it is fairly straightforward to implement and customize to your own requirements.
Check out the Linux Firewall mini setup guide which demonstrates the use of iptables in Linux. Here I demonstrate a few basic commands and rules and explained how we can allow and deny specific traffic on your Linux server. The scenario is for typical web server allowing only HTTP, HTTPS and SSH. Host based firewalls are often overlooked relying solely on perimeter defenses however are an important aspect of protecting your endpoint whether that is on a server or workstation. Iptables in built into Linux is a pretty capable command line based stateful firewall. Once you have the hang on the syntax it is fairly straightforward to implement and customize to your own requirements.