AAA and RADIUS through the Network Policy Server (NPS) role in Windows Server 2012 R2
I thought I would cover a quick post to demonstrate setting up Active Directory authentication for a Cisco router or switch IOS login. This will be using AAA and RADIUS through the Network Policy Server (NPS) role in Windows Server 2012 R2 to authenticate users in Active Directory on Cisco IOS devices.
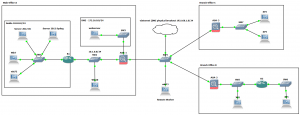
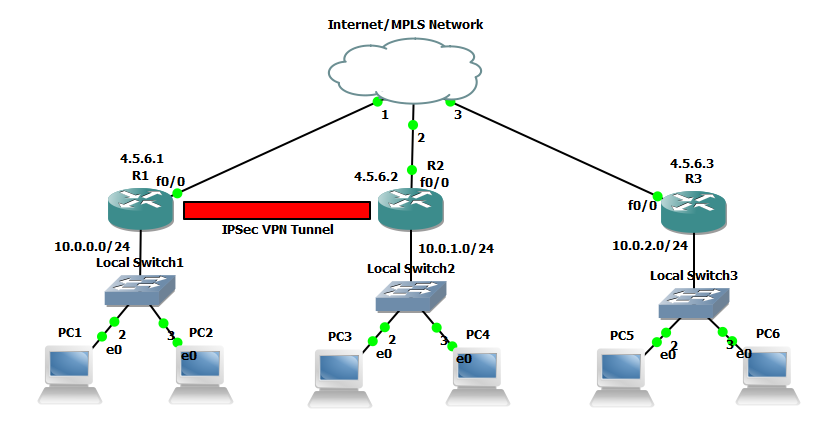
As with all my labs a picture paints a thousand words so here is the GNS3 Network topology we will be using, this is also being used for 802.1x which will be covered in later post:
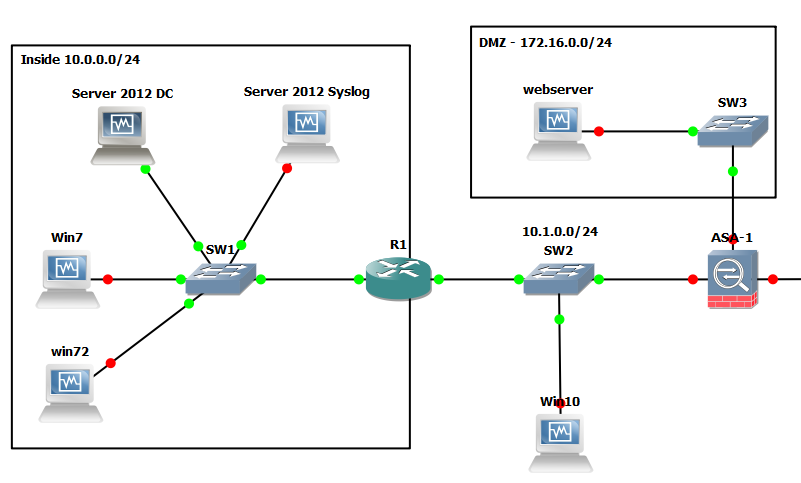
So here is quick run down on the gear we will be using just for this lab:
R1: Cisco IOS (C7200-ADVENTERPRISEk9-M), Version 15.2(4)S4
Server 2012 DC: Windows Server 2012 R2 ( Active Directory Domain Services and Network Policy Server role.
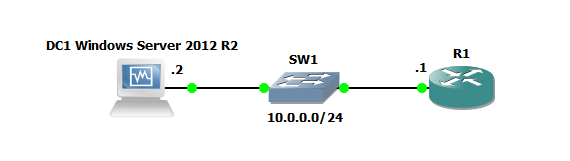
Just to demonstrate a lab as simple as the below could also be used to test this:
Active Directory Configuration:
I will be assuming that AD and the NPS role have already been installed. Prior to jumping into the NPS configuration you will need to create an AD group for the users that will be logging into the Cisco equipment, add a couple of test users to this group. In my case I have simply created a group called ‘Radius’ and have added the user ‘Adam’.
Open the NPS console.
Right click on the NPS(Local) tree node and select ‘Register server in Active Directory’:
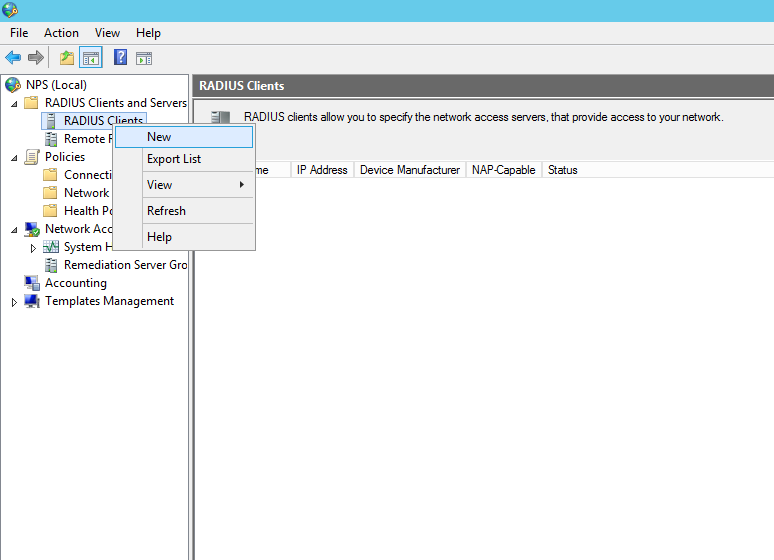
Now create the Radius clients, in our this case this is R1:
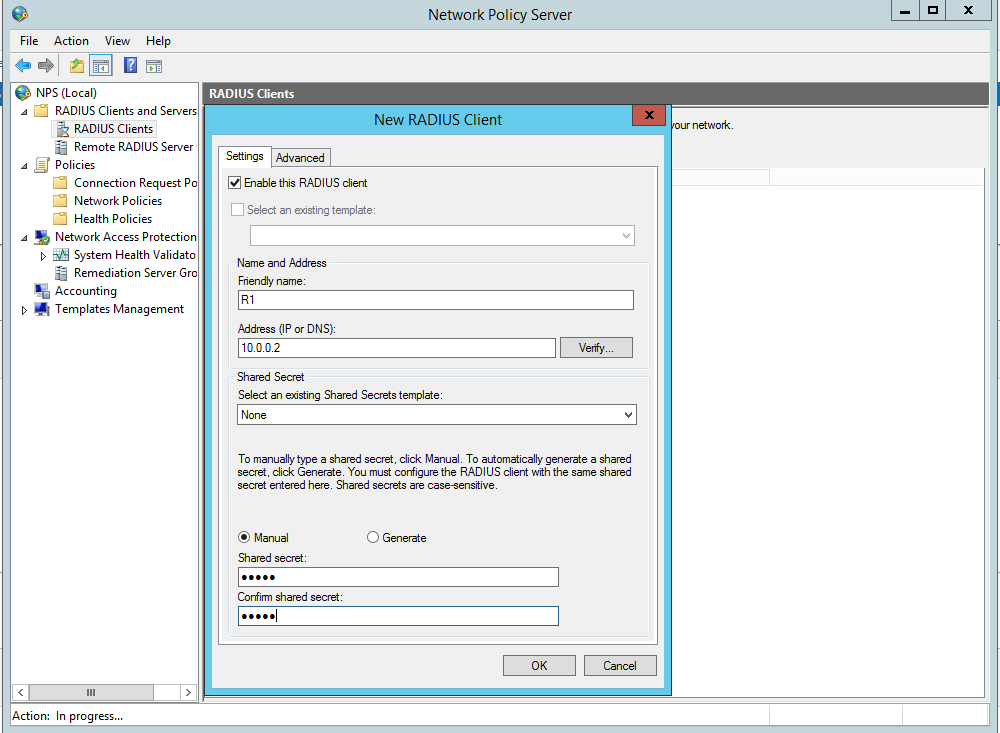
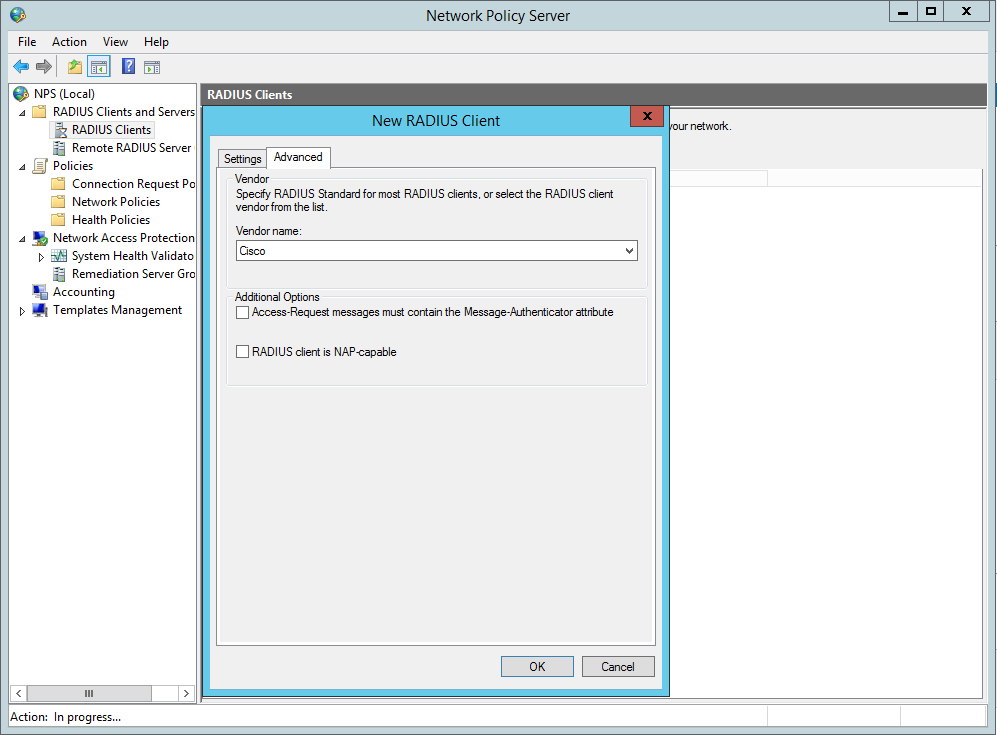
Now we need to configure the Network policy:
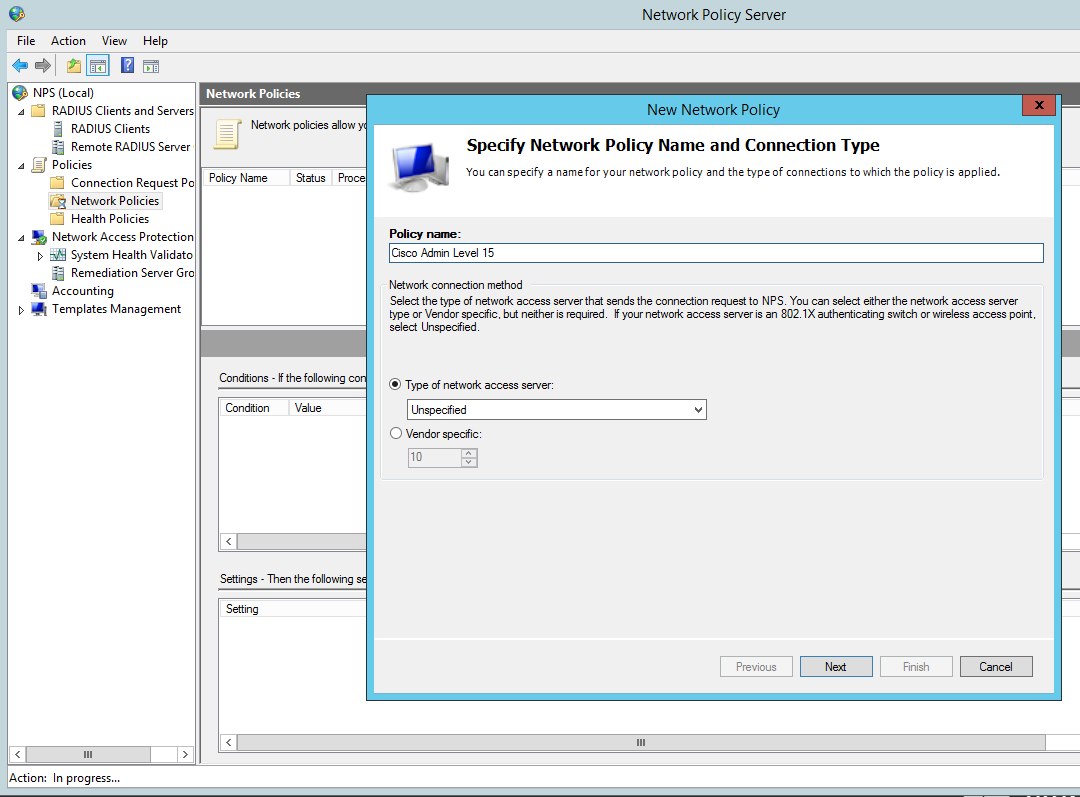
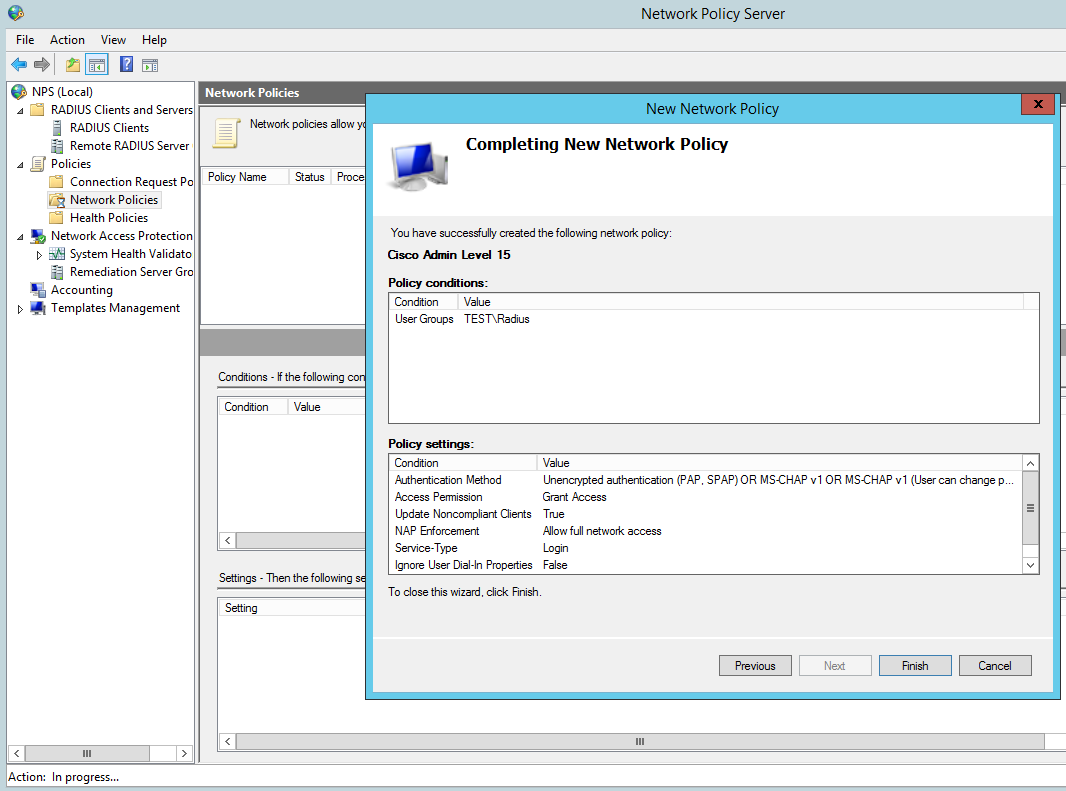
Add our ‘Radius’ AD group. You can tighten the control here by specifying further conditions such as the ‘friendly name’ (R1) or the local IPV4 address of the radius client, in a production environment you would want to lock this down further for now we are just going to add the the user group to authenticate:
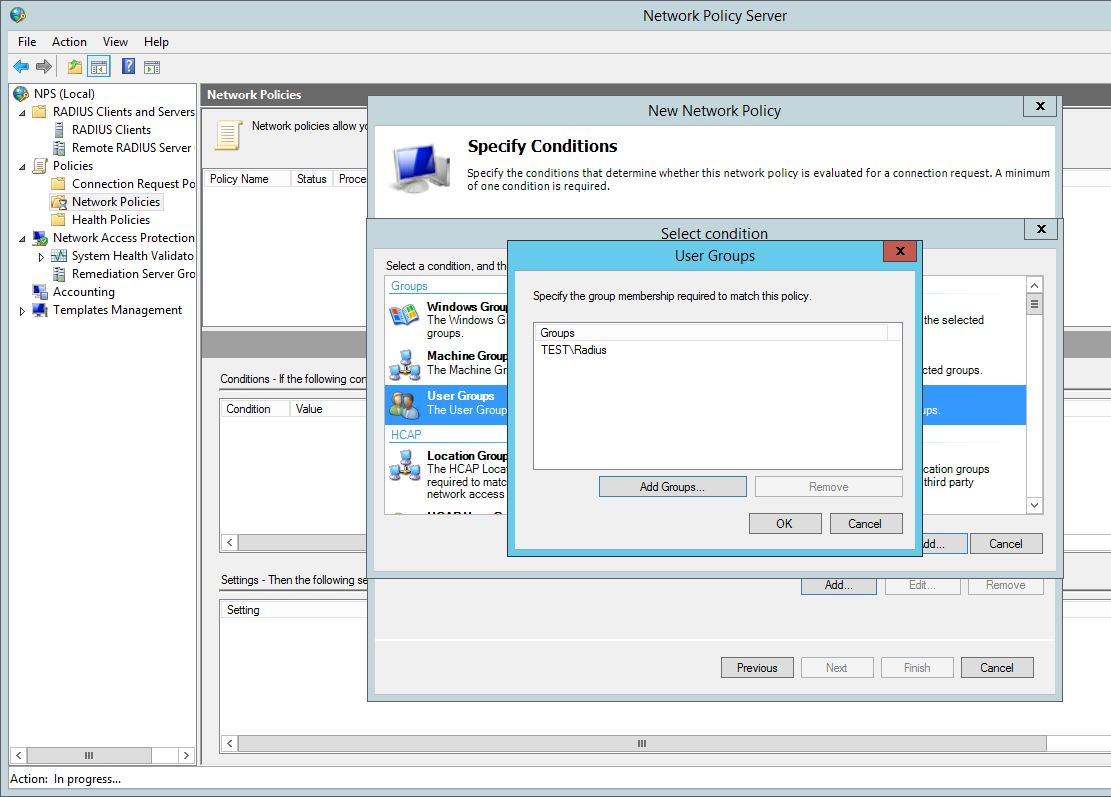
Grant Access for this group:
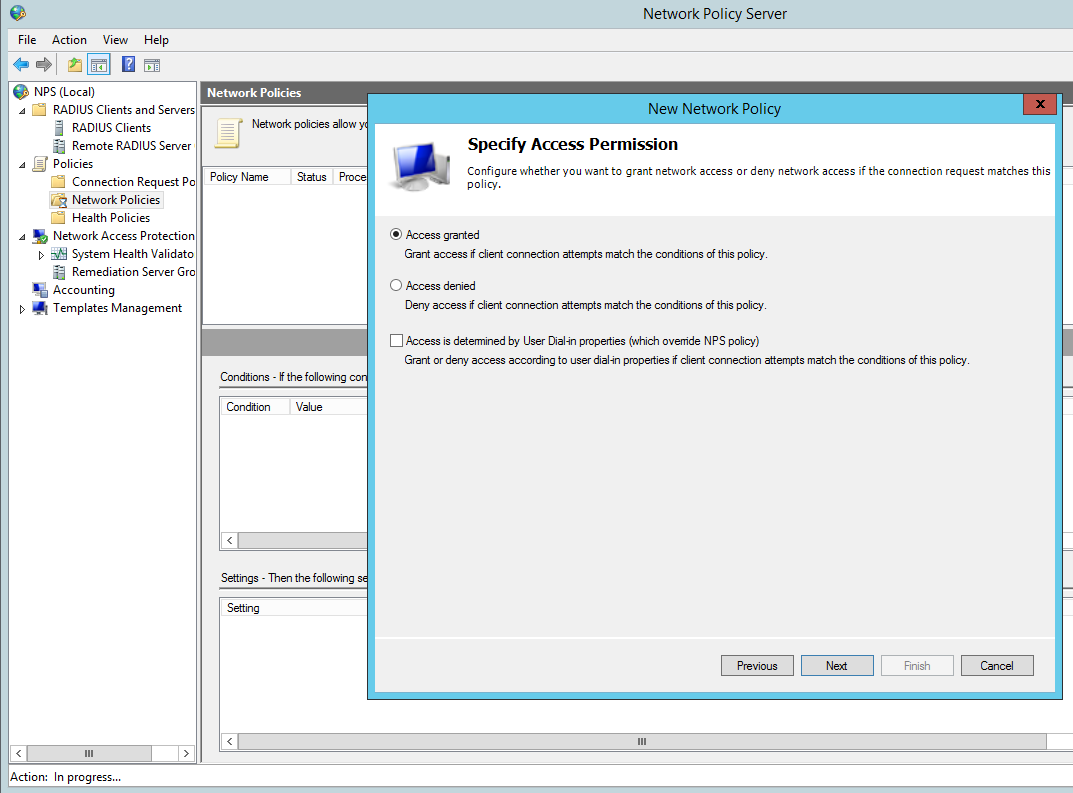
Configure the appropriate authentication methods:
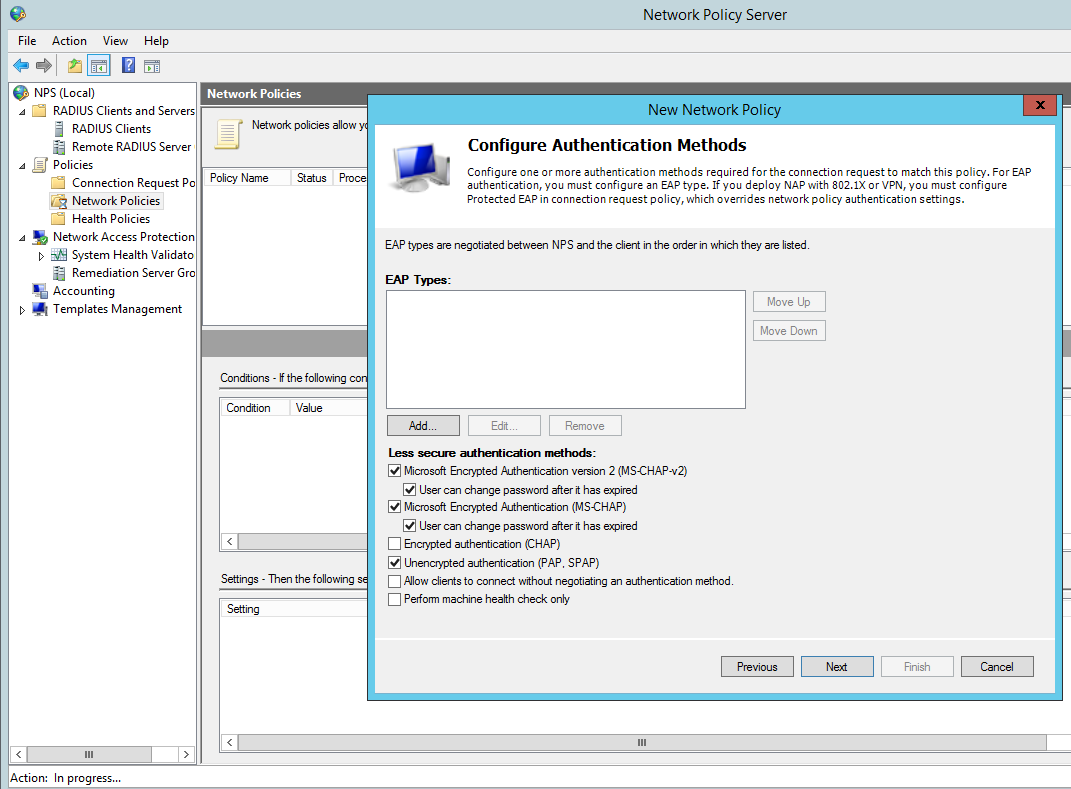
Change the Standard Radius Attributes by removing ‘Framed-Protocol – PPP’. Edit the ‘Service-Type’ value to ‘Login’:
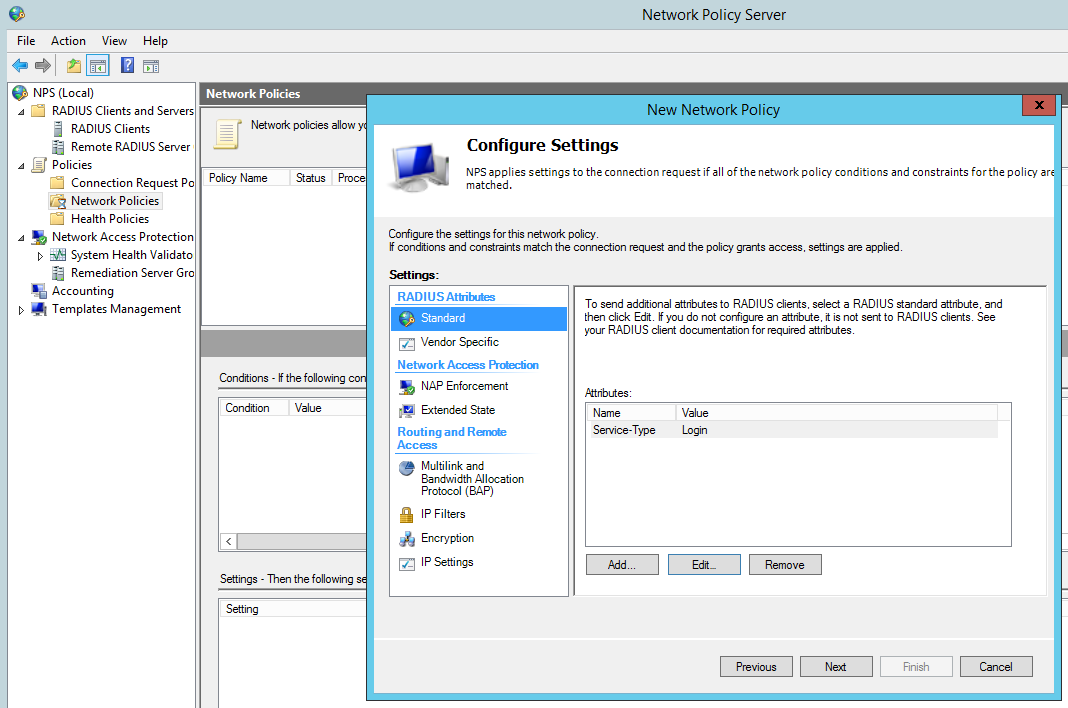
Add a Vendor specific attribute, this allows the radius server to pass the privilege level though the cisco router which we shall see later in the debugging. The value needs to read ‘shell:priv-lvl=15′.
You can create several policies for the different privilege levels. For example you could create a group in AD called ‘Cisco Users Priv 1’, associate this group to a policy and in the below option use the value ‘shell:priv-lvl=1′. When that user logs in the policy will match that user and the NPS use the matched policy passing privilege level 1 through to the router or switch.
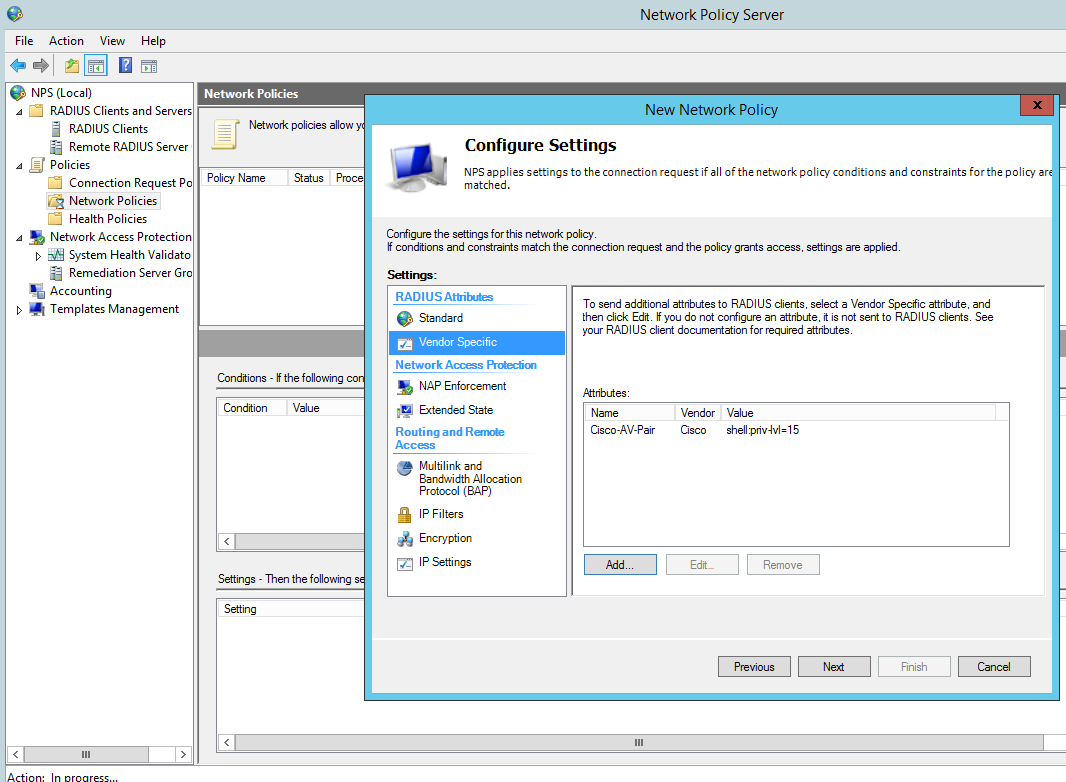
Then Finish:
Cisco IOS configuration
Create a a user with privilege level 15, we wil use this as our fall back should the router not be able to contact the radius server it will use the local AAA database.
R1(config)#username Admin privilege 15 secret cisco12345
Enable AAA:
R1(config)#aaa new-model
Now we will setup the main parts to the radius configuration, tell the switch we would like to use radius and the group RAD_SERVERS:
R1(config)#aaa group server radius RAD_SERVERS
Specify the radius server that we would like to use in our case 10.0.0.2 is our NPS, the auth and acc ports and also the secure key we used:
R1(config-sg-radius)#server-private 10.0.0.2 auth-port 1812 acct-port 1813 key cisco
R1(config-sg-radius)#exit
Specify that for the default login for authentication an authorization that we want to use the group called RAD_SERVERS that we have just created and if that fails we use the local database. This is particularly important so we do not lock ourselves out on the router:
R1(config)#aaa authentication login default group RAD_SERVERS local
R1(config)#aaa authorization exec default group RAD_SERVERS local if-authenticated
All together this looks like the below:
R1(config)#aaa group server radius RAD_SERVERS
R1(config-sg-radius)#server-private 10.0.0.2 auth-port 1812 acct-port 1813 key cisco
R1(config-sg-radius)#exit
R1(config)#aaa authentication login default group RAD_SERVERS local
R1(config)#aaa authorization exec default group RAD_SERVERS local if-authenticated
R1(config)#aaa authorization console
We can test simply by logging out and back in.
Troubleshooting
It obviously goes without saying you need to test the authentication to the Radius server, exit right out of the console and log back in using your AD credentials.
If all has been configured correctly you should be able to login. its also worth testing the fall back option configured for local AAA authentication. We can do this just simply stopping the NPS service then try the local credentials, again all being configured correctly you should be able to login.
There are a few useful debugging commands we can use to monitor and troubleshoot the authentication these being:
R1#debug aaa authentication
AAA Authentication debugging is on
R1#debug aaa authorization
AAA Authorization debugging is on
R1#debug radius
Radius protocol debugging is on
Radius protocol brief debugging is off
Radius protocol verbose debugging is off
Radius packet hex dump debugging is off
Radius packet protocol debugging is on
Radius elog debugging debugging is off
Radius packet retransmission debugging is off
Radius server fail-over debugging is off
Radius elog debugging debugging is off
R1#
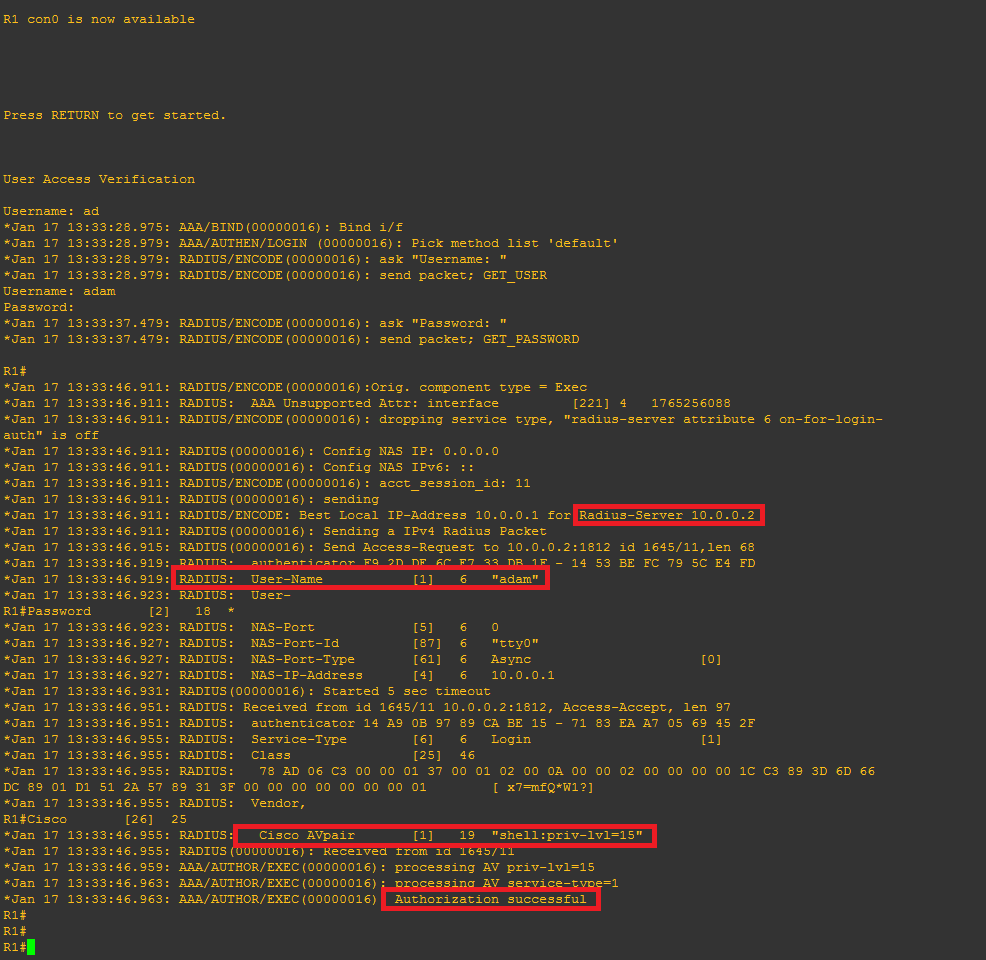
This time when we login we can see the debug information for an attempted login, it should look similar to this, note the highlighted area’s:
I hope this has been informative.
 As an industry we need more information security defenders to play the role of the blueteam in the Enterprise. All too often the IT Team receive a pentest report with a list of red criticals and are immediately overwhelmed with issues to fix. Whilst an organization has regular pentests it has the danger of lulling itself into a feeling of ‘doing the right thing’ however if all they are doing is getting a pentest and not re-mediating the issues then its a waste of time and money. This is a pessimistic view however it is usually the case that more vulnerabilities are released that the IT know what to do with. The IT team tend to either not have enough resource or they don’t have the skills to fix the issues, usually the first being being the case. Penetration testing needs to be more than just a test, it needs to be a more proactive engagement with after test help and support for the enterprise should they need it.
As an industry we need more information security defenders to play the role of the blueteam in the Enterprise. All too often the IT Team receive a pentest report with a list of red criticals and are immediately overwhelmed with issues to fix. Whilst an organization has regular pentests it has the danger of lulling itself into a feeling of ‘doing the right thing’ however if all they are doing is getting a pentest and not re-mediating the issues then its a waste of time and money. This is a pessimistic view however it is usually the case that more vulnerabilities are released that the IT know what to do with. The IT team tend to either not have enough resource or they don’t have the skills to fix the issues, usually the first being being the case. Penetration testing needs to be more than just a test, it needs to be a more proactive engagement with after test help and support for the enterprise should they need it.
 I thought I would share with you all a new podcast I have been listening to (well new to me). Risky Business, as taken from the website ‘Risky Business was established in February, 2007. It takes a lighthearted look at information security news and features!’ – I’ve found this weeks episode #399 particularly interesting, it contained news stories that are current at the moment, with just the right amount of technical detail to keep me listening. Notably the stories of the week that were discussed were around the iPhone FBI saga that started last week, GLibc vulnerability and interestingly the new NIST Cyber Security framework which was discussed by Cris Thomas, a.k.a. Space Rogue.
I thought I would share with you all a new podcast I have been listening to (well new to me). Risky Business, as taken from the website ‘Risky Business was established in February, 2007. It takes a lighthearted look at information security news and features!’ – I’ve found this weeks episode #399 particularly interesting, it contained news stories that are current at the moment, with just the right amount of technical detail to keep me listening. Notably the stories of the week that were discussed were around the iPhone FBI saga that started last week, GLibc vulnerability and interestingly the new NIST Cyber Security framework which was discussed by Cris Thomas, a.k.a. Space Rogue.
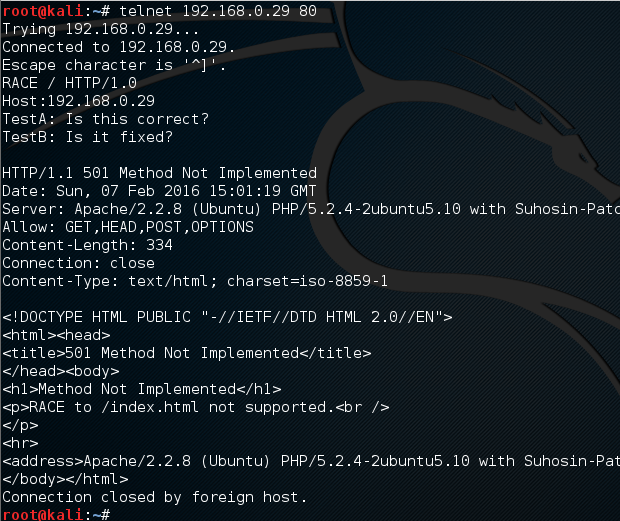
 Many vulnerability scanners will often bring back HTTP TRACE TRACK Methods Allowed against Apache and Microsoft web servers of the older generation. TRACE is usually associated with Apache and TRACK for Microsoft. This has a CVSS score of 4.3 and is a relatively easy fix. Clearly the older generation operating systems should be migrated to a supported platform, both the later distributions of Ubuntu and Microsoft 2012 R2 do not allow these methods to be used. However a simple way to validate this finding is to use telnet to connect to the web server on port 80, once connected you can type something similar to the following for each method. The ‘Host’, ‘TestA’ and ‘TestB’ aren’t needed however if you use some custom text you will be sure to see it echoed back by the web server if trace is enabled.
Many vulnerability scanners will often bring back HTTP TRACE TRACK Methods Allowed against Apache and Microsoft web servers of the older generation. TRACE is usually associated with Apache and TRACK for Microsoft. This has a CVSS score of 4.3 and is a relatively easy fix. Clearly the older generation operating systems should be migrated to a supported platform, both the later distributions of Ubuntu and Microsoft 2012 R2 do not allow these methods to be used. However a simple way to validate this finding is to use telnet to connect to the web server on port 80, once connected you can type something similar to the following for each method. The ‘Host’, ‘TestA’ and ‘TestB’ aren’t needed however if you use some custom text you will be sure to see it echoed back by the web server if trace is enabled.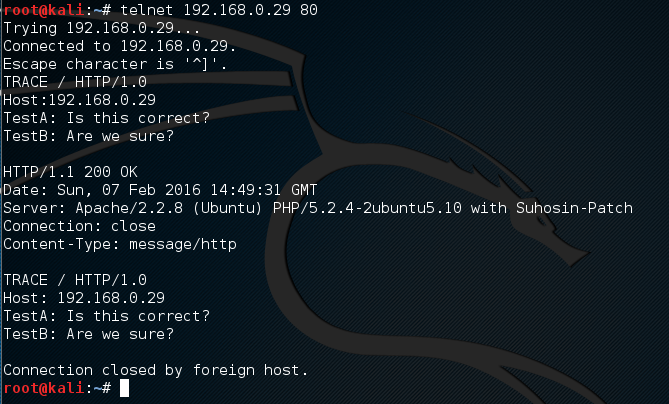
 Email Relaying with mailtrap.io
Email Relaying with mailtrap.io