Quick Tip: Enabling Active Directory DNS query logging for Windows Server 2012 R2.
DNS query logging isn’t enabled by default in Windows Server 2012 R2 within the DNS server role. DNS ‘events’ are enabled by default just not activity events which capture lookup’s from users machine for example. This is super useful for incident response type scenarios, investigations, troubleshooting and not to mention malware or crypto type ware that’s looking to phone home to command and control. We can enable it like so:
Firstly there is a hotfix that needs to be applied to Windows Server 2012 R2 this can be found here http://support.microsoft.com/kb/2956577 you can read more about this here. This essential adds query logging and change auditing to Windows DNS servers.
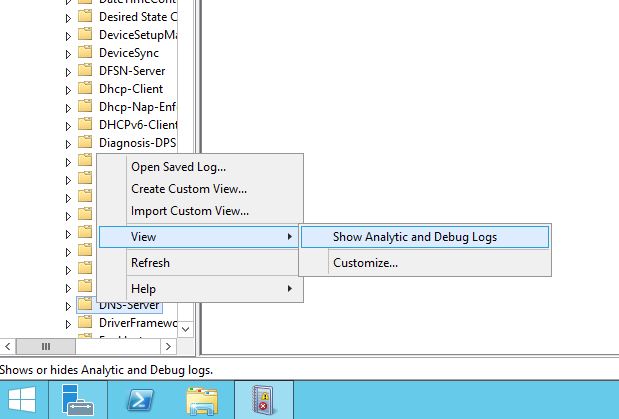
Next go to the event viewer, under ‘Application and Services’, ‘Microsoft’. ‘Windows’, right click on ‘DNS-Server’ select ‘View’ following it across and select ‘Show Analystic and Debug Logs’ like below:
(Note you will actually need to left click on ‘DNS-Server’ first then right click on it otherwise the view option won’t show up.)
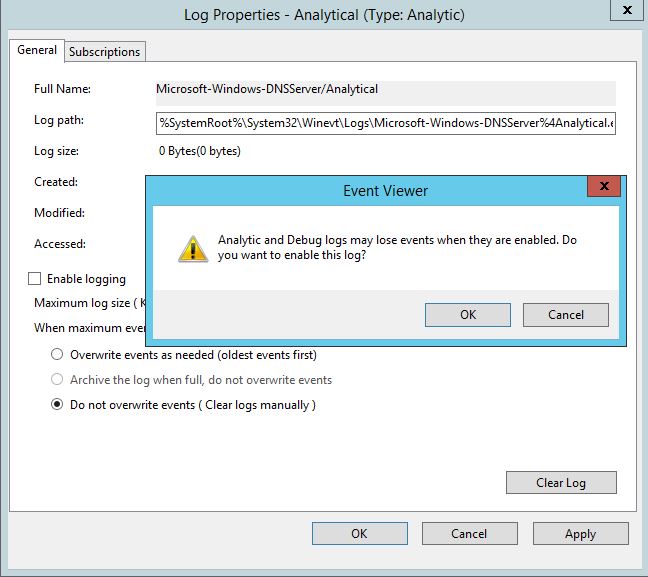
This will display the Analytical log, right click on this and select properties, enable logging and Do not overwrite events. Like below:
Click ok and your done.
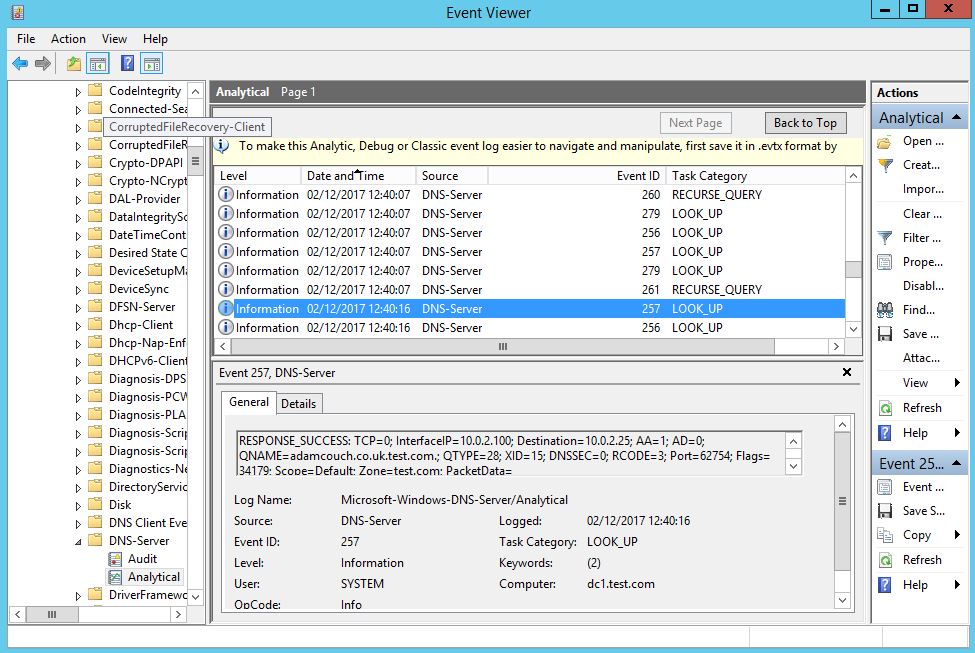
We can verify the query logging is working in our lab by simple making a DNS request from a workstation, we will see the query in the event view under the ‘Analytical’ log like below:
Super. Now we can see which workstation IP address has made the query, and what exactly is being queried. In the above example we can see that a destination address, 10.0.2.25 a Windows 7 domain joined workstation has requested adamcouch.co.uk. Dns query Logs, yay! Hope this helps.