Protecting the LSASS.exe process with RunAsPPL is in an important part of hardening Windows Server 2012 R2 and Windows 8.1. Credential theft is trivial with Administrative level privileges, I have blogged about the use of mimikatz several times in the past. This post is here to try and raise awareness of what we can do to help protect against adversaries getting there hands on creds. Doing everything we can to try to protect against credential theft is clearly important. There are now advances in Windows 10 and Server 2016 that help mitigate this with Credential Guard, however earlier versions of windows are still vulnerable. The Local Security Authority Server Service (LSASS) process in windows is responsible for authenticating/validating users that login via local console or remote desktop. Tools such as mimikatz interact with the lsass process to extract credentials, whether that’s directly on the server or workstation at the time of attack or dumping the lsass process to a file and extracting credentials off line at a later stage.
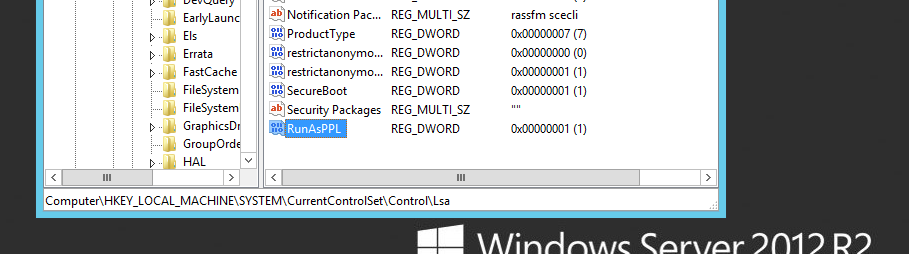
With Windows Server 2012 R2 and 8.1 there is a feature called LSA (Local Security Authority) Protection according to the following Microsoft page we are able to run LSASS as a protected process. This essentially prevents mimikatz from working correctly out of the box. In addition to this it will prevent you from being able to dump the lsass process to a file through task manager. With some tweaking you can get around this however a driver or signature verification code would need to be added into the mix for it to work properly and be able to interact with the lsass process as a protected process (this can be monitored though through the event log). The following registry change can be added to enable the protection at HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa adding a new DWORD entry of “RunAsPPL” with a value of 1. This does require a reboot however.
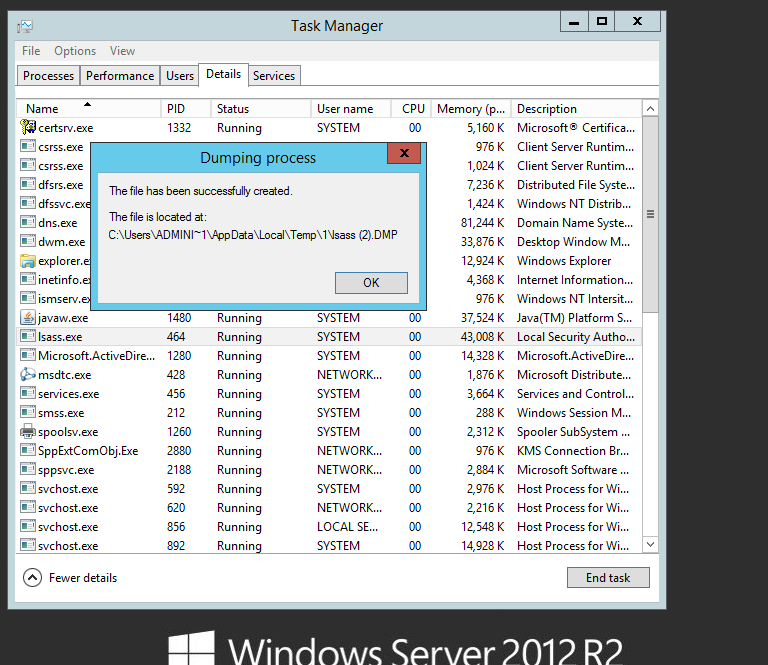
Lets see it in action on Windows Server 2012 R2. Before the change you can see I am able to dump the lsass process to a file from task manager:
This file could then be used with mimikatz on or offline to extract NTLM password hashes for cached credentials.
Lets make the change, and reboot:
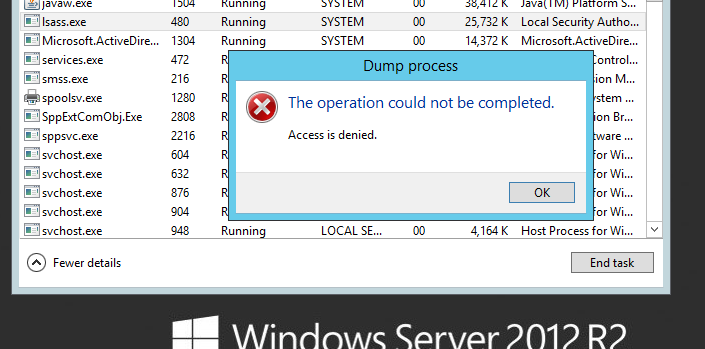
And after:
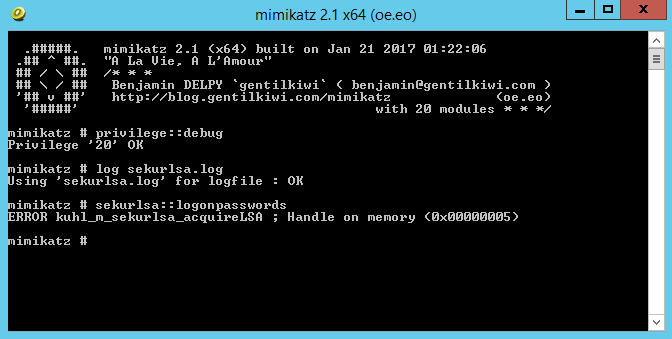
Good! And if we try to run mimikatz on the server:
This doesn’t offer total protection however if we can slow down our adversaries and try to stay one step ahead we are in a better place than before. Clearly if you have plugins in your environment that need to interact with the lsass process this may break things so testing is a must, there is an auditing mode highlighted here that will help identify any that fail.
Hope this helps.