All too often web servers are setup with fairly standard configuration. The HTTP Headers display various information from time stamps, cookie info and also server version.
Server version information especially should be removed from the HTTP headers as it allows an attacker to identify what the underlying server and web server version is. If vulnerabilities lie in the stated version, an attacker can concentrate there efforts towards that version identified on your system more easily.
The below configurations should be set for minimal server version info.
Linux/Apache/PHP:
In the /etc/php5/apache2/php.ini file find the line ‘expose_php = On’ and set the parameter from ‘On’ to ‘Off’ as below:
; Decides whether PHP may expose the fact that it is installed on the server ; (e.g. by adding its signature to the Web server header). It is no security ; threat in any way, but it makes it possible to determine whether you use PHP ; on your server or not. ; http://php.net/expose-php expose_php = Off
This will remove the ‘X-Powered-by’ option from the HTTP header thus removing your PHP version and OS version information.
In the /etc/apache2/conf-available/security.conf locate the ‘Server Tokens Full’ line and change the parameter from ‘Full’ to ‘Prod’ this will give the least amount of information. Unfortunately without changing this hard-coded parameter and recompiling apache yourself there is no way to reduce this information any further.
# ServerTokens # This directive configures what you return as the Server HTTP response # Header. The default is 'Full' which sends information about the OS-Type # and compiled in modules. # Set to one of: Full | OS | Minimal | Minor | Major | Prod # where Full conveys the most information, and Prod the least. #ServerTokens Minimal #ServerTokens OS #ServerTokens Full ServerTokens Prod
In the same file locate the ‘ServerSignature On’ line and change the parameter from ‘On’ to ‘Off’, or comment out the existing line and add a new one in with the ‘Off’ option as below.
The ServerSignature isn’t actually information from or displayed in the HTTP headers, it is however information that is displayed at the bottom of for example a 404, 403 default page, which again will give away information about your system. Better still use a custom 404 or 403 page however if you don’t have custom pages this is the next best thing.
# Optionally add a line containing the server version and virtual host # name to server-generated pages (internal error documents, FTP directory # listings, mod_status and mod_info output etc., but not CGI generated # documents or custom error documents). # Set to "EMail" to also include a mailto: link to the ServerAdmin. # Set to one of: On | Off | EMail ServerSignature Off #ServerSignature On
And as usual you should test these configurations out in a test environment first before your main production web servers.

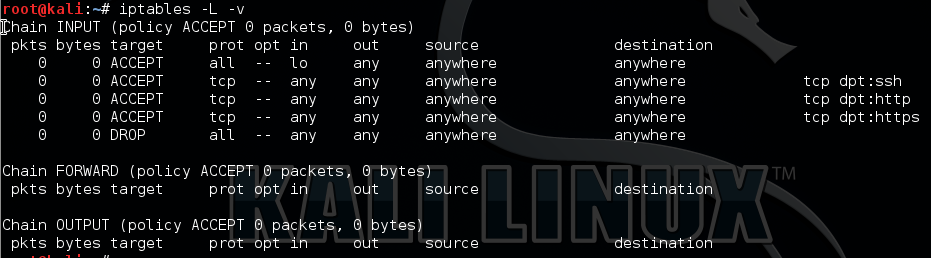
 Check out the Linux Firewall mini setup guide which demonstrates the use of iptables in Linux. Here I demonstrate a few basic commands and rules and explained how we can allow and deny specific traffic on your Linux server. The scenario is for typical web server allowing only HTTP, HTTPS and SSH. Host based firewalls are often overlooked relying solely on perimeter defenses however are an important aspect of protecting your endpoint whether that is on a server or workstation. Iptables in built into Linux is a pretty capable command line based stateful firewall. Once you have the hang on the syntax it is fairly straightforward to implement and customize to your own requirements.
Check out the Linux Firewall mini setup guide which demonstrates the use of iptables in Linux. Here I demonstrate a few basic commands and rules and explained how we can allow and deny specific traffic on your Linux server. The scenario is for typical web server allowing only HTTP, HTTPS and SSH. Host based firewalls are often overlooked relying solely on perimeter defenses however are an important aspect of protecting your endpoint whether that is on a server or workstation. Iptables in built into Linux is a pretty capable command line based stateful firewall. Once you have the hang on the syntax it is fairly straightforward to implement and customize to your own requirements.