Fixing Metasploit database cache
Just a quick reminder to myself and others of how to fix the Metasploit database cache not built issue. When we use Metasploit the search is super slow and returns the ‘slow search warning’ This where you find either the database isn’t connected or when you try to search for a vulnerability the return is ‘[!] Module database cache not built yet, using slow search’ due to the database not being connected like below: This doesn’t seem to be a huge issue and the search still works however its a fairly easy fix and makes the searching significantly quicker. I’ve posted this as I’m usually finding myself having forgotten the syntax to fix it after rebuilding a kali vm, and searching around various other posts on the internet for it, so here it is:
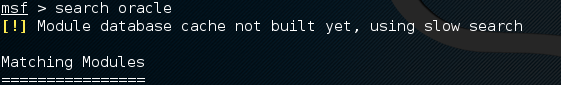
If we check the database in Metasploit with db_status we find the below error:
![]()
So to fix the issue:
Start the postgresql service and ensure it starts at startup:
![]()
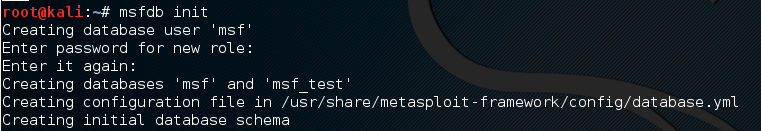
Initialize the msf database with:
Load msfconsole and recheck the database you should find this is now connected:
![]()
Finally rebuild the db cache, give it a few minutes and you should find the search instantaneous :
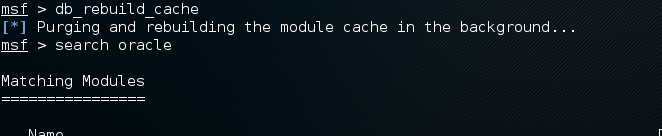
et voila!

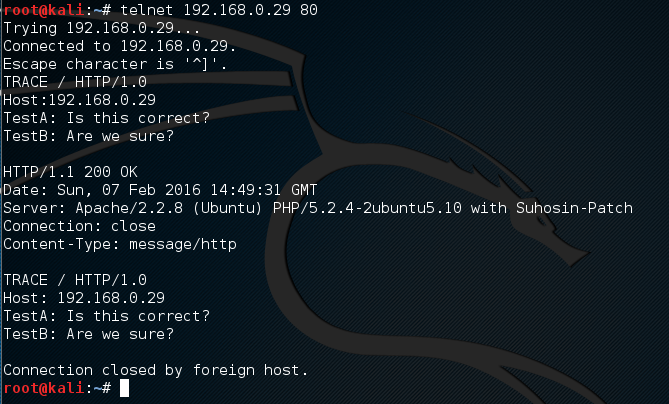
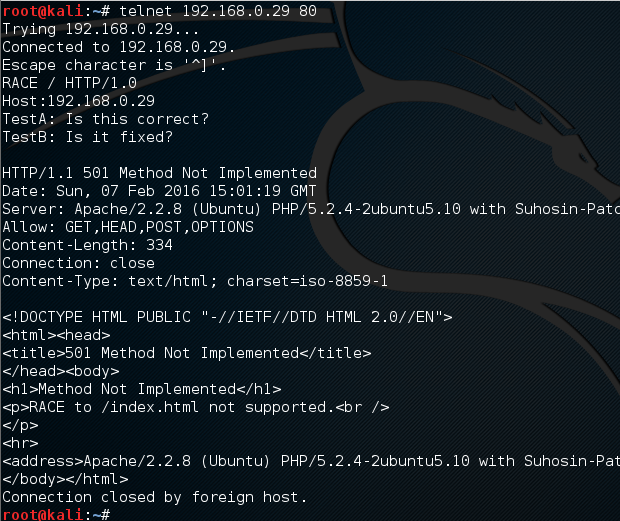
 Many vulnerability scanners will often bring back HTTP TRACE TRACK Methods Allowed against Apache and Microsoft web servers of the older generation. TRACE is usually associated with Apache and TRACK for Microsoft. This has a CVSS score of 4.3 and is a relatively easy fix. Clearly the older generation operating systems should be migrated to a supported platform, both the later distributions of Ubuntu and Microsoft 2012 R2 do not allow these methods to be used. However a simple way to validate this finding is to use telnet to connect to the web server on port 80, once connected you can type something similar to the following for each method. The ‘Host’, ‘TestA’ and ‘TestB’ aren’t needed however if you use some custom text you will be sure to see it echoed back by the web server if trace is enabled.
Many vulnerability scanners will often bring back HTTP TRACE TRACK Methods Allowed against Apache and Microsoft web servers of the older generation. TRACE is usually associated with Apache and TRACK for Microsoft. This has a CVSS score of 4.3 and is a relatively easy fix. Clearly the older generation operating systems should be migrated to a supported platform, both the later distributions of Ubuntu and Microsoft 2012 R2 do not allow these methods to be used. However a simple way to validate this finding is to use telnet to connect to the web server on port 80, once connected you can type something similar to the following for each method. The ‘Host’, ‘TestA’ and ‘TestB’ aren’t needed however if you use some custom text you will be sure to see it echoed back by the web server if trace is enabled.